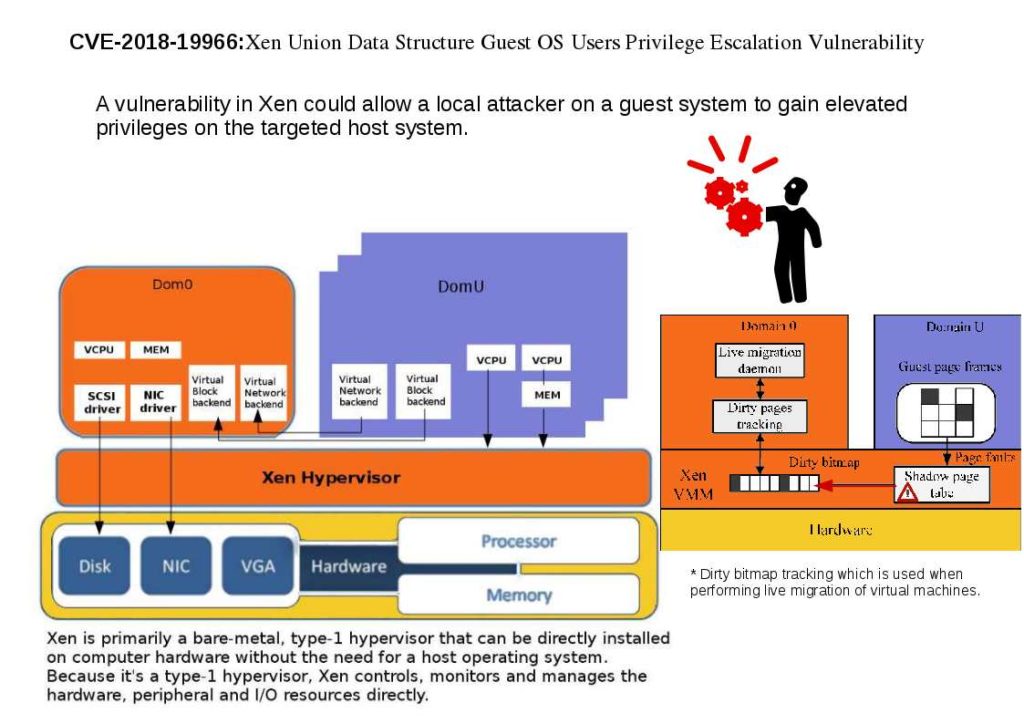
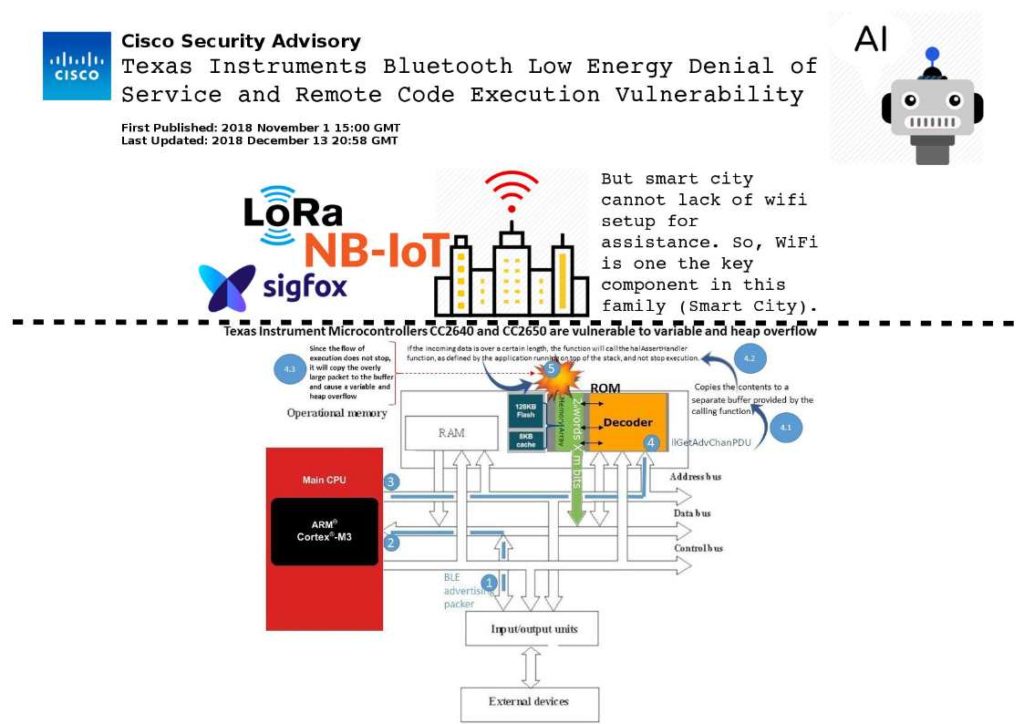
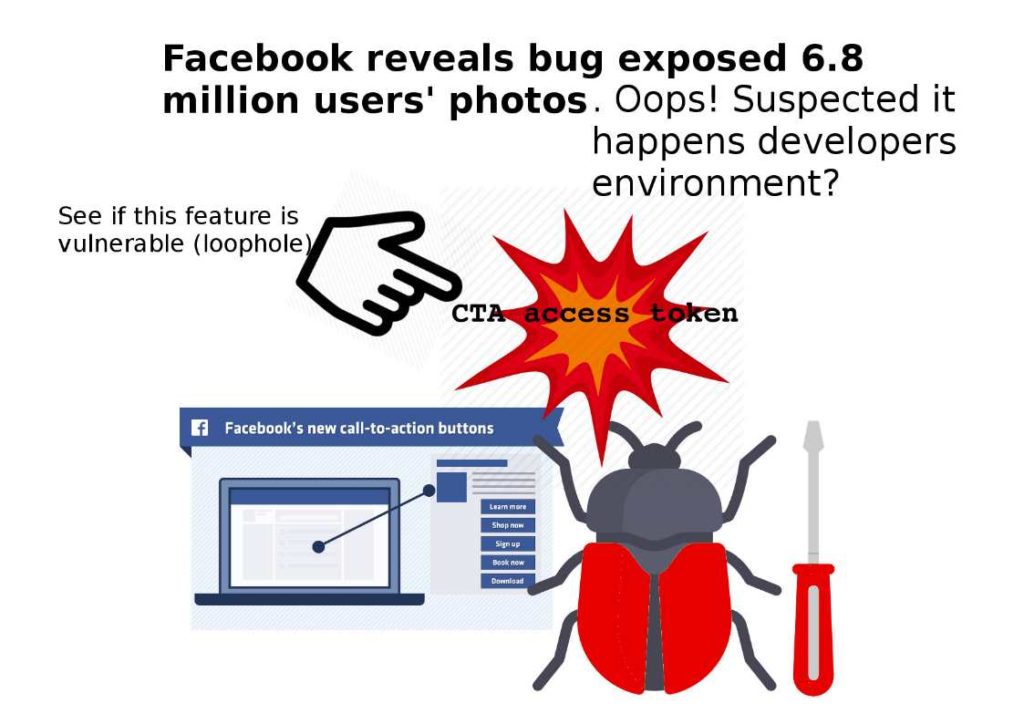
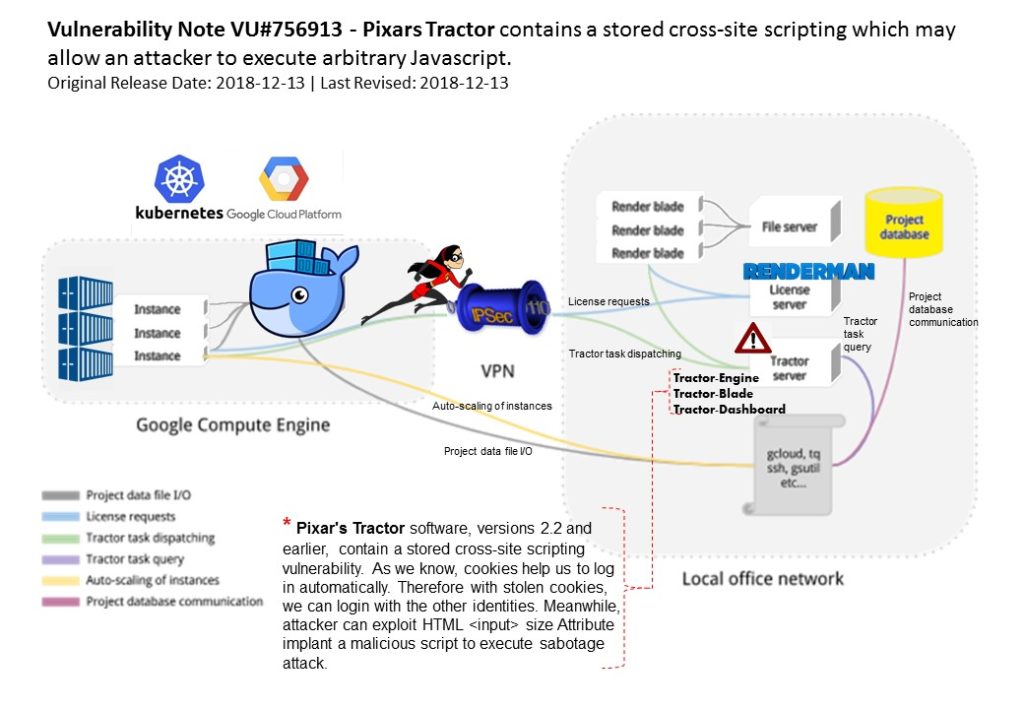
Preface: Quasar, a legitimate open-source remote administration tool. It is a fast and light-weight remote administration tool coded in C#.
Background: APT actors have adapted Quasar and created modified minor (1.3.4.0) and major (2.0.0.0 and 2.0.0.1) versions. Since the re-engineering Quasar client will be mimics a Mozilla Firefox 48 browser running on Windows 8.1 or mimics an Apple Safari 7.0.3 browser running on Mac OS X 10.9.3 in order to evade IDS monitoring. However there are way lets security operation center find their fingerprint. The distinctive first 4 bytes of the payload can be used to identify Quasar traffic.
As a result, below analytic way can be enforce the detective control:
Signature 1: TCP Payload Size Tracking
Signature 2: IP Lookup User-Agent String, HyperText Transfer Protocol Header Host, and HyperText Transfer Protocol Header URI
Signature 3: Hidden HTTP Request User-Agent String and Time-to-Live
More details can be found below url: https://unit42.paloaltonetworks.com/unit42-downeks-and-quasar-rat-used-in-recent-targeted-attacks-against-governments/