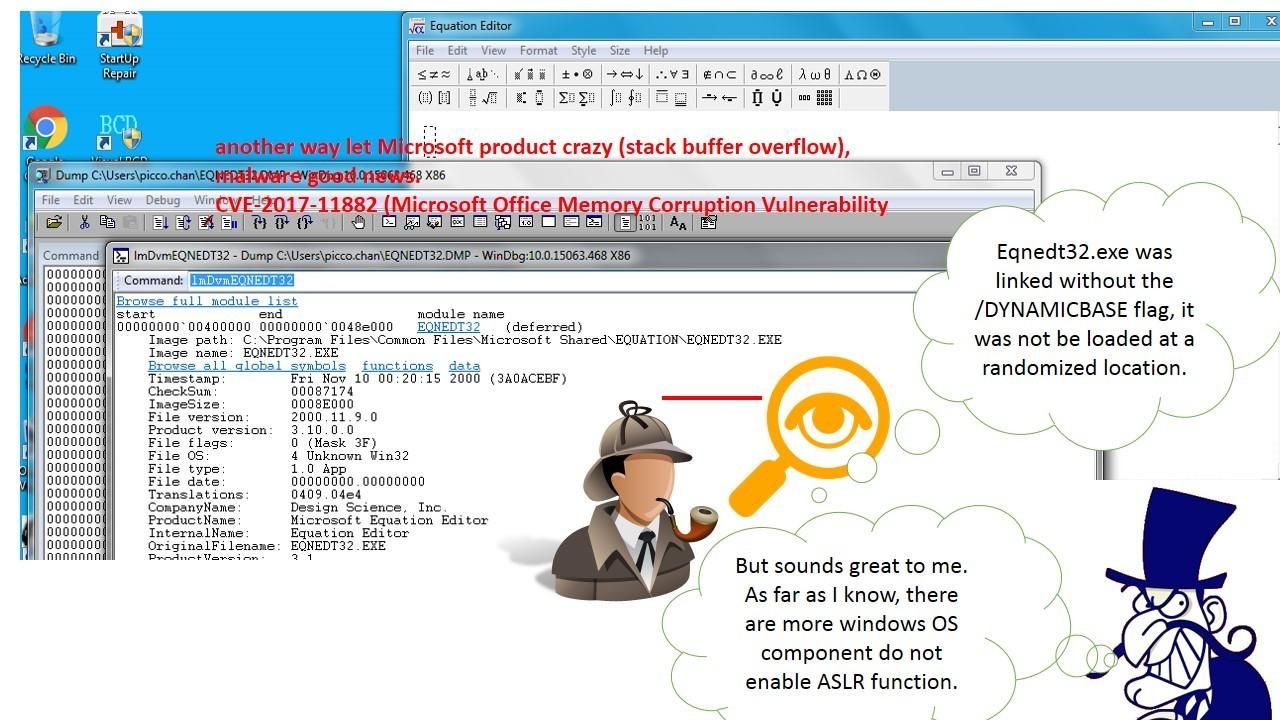
Seems heard a vulnerability occurs on microsoft product did not trigger your interest. The easy way for IT guy to mitigate the risk is conduct a patch update. But CVE-2017-11882 heads up the world that there are more windows OS components did not included ASLR protection feature. May be you could say Microsoft product do not relies on ASLR since they has Data Execution Prevention (DEP). We known Data Execution Prevention (DEP) is a system-level memory protection feature. However a practical example of CVE-2017-11882 occured on Microsoft office product could compromised your machine. Hacker more focus to dig out vulnerability on word processing product since human relies on electronic documentation daily. Microsoft release the patch to mitigate this risk (see below). But a reminder to the world there are more MS components do not enable randomizes address function. Yes, no randomizes address function will be benefits to hacker. Which industry on demand to use MS equation editor function. Scientist, high tech industry especially military and nuclear power facilities management.
I’d must test with you here. Which is not something I normally do! I take pleasure in reading a publish that can make individuals think. Also, thanks for allowing me to remark!