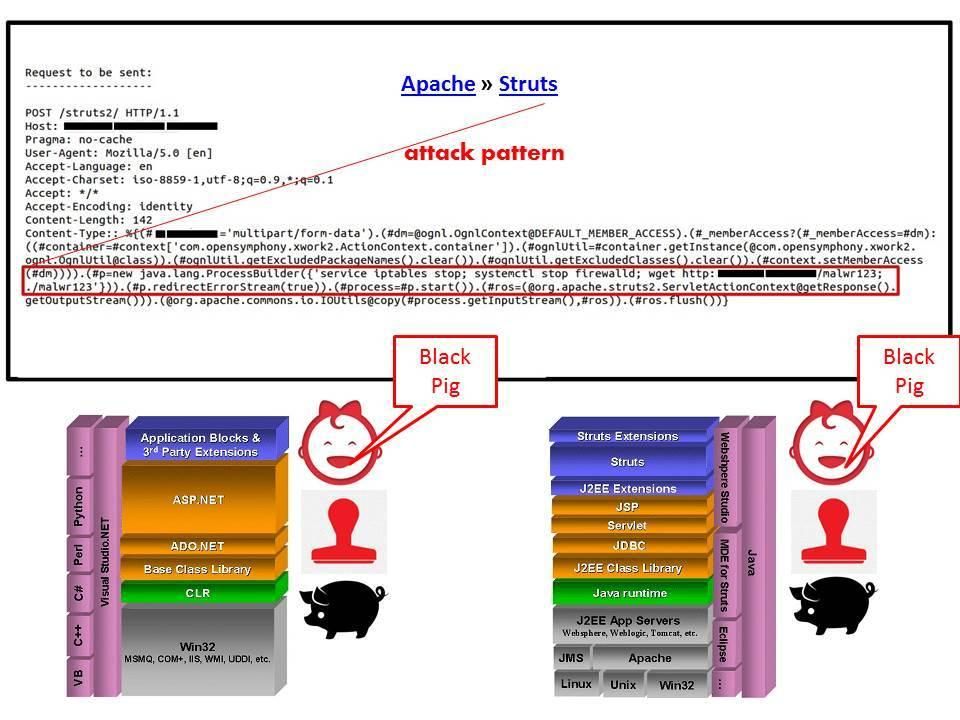
We believed that Apache web server more secure than Microsoft IIS Web server so far. However the most recent security incidents told the world the products of Apache not secure anymore! For instance, a critical vulnerability on Apache Struts encountered a serious vulnerability on Mar 2017 (CVE-2017-5638). As of today, there are total 4 vulnerabilities (CVE-2017-5638,CVE-2017-7672,CVE-2017-9787,CVE-2017-9791) which jeopardize Enterprise firms. It looks that the slogan “Apache products more secure than Microsoft web products” is not valid anymore! Remark: When I was young, a black pig symbol let the kindergarten student understand their performance. We now know both brand name are receiving black pig stamp chop.
What will be the impact?
For more details, please see below url for references:
4-traders.com (APACHE-CORPORATION)
Looks negative Cisco also the victim on this case. For more details, please see below url for reference.
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20170909-struts2-rce
Cisco announced that no workarounds available in the moment. However if your IT campus install Snort IDS. New yara rules will be fight against the attack. It looks that cyber attack is one of the business development channel!
Responsibility and Realistic
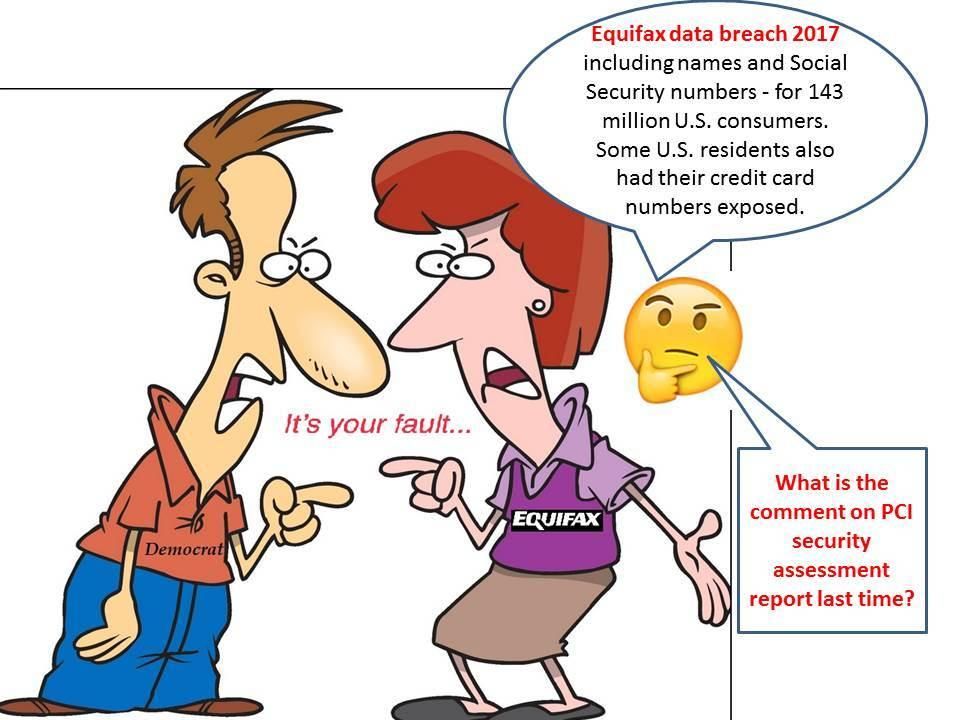
About Equifax data breach on 29th Jul 2017, CIO and CSO are retiring. The flaw focusing to the company with poor software patch management. The investigation team highlight two major problems. The company are using open source and without update the patch on Apache struts product immediately. But think it over, the server side contained client credit card information. It looks that no one else is going to discuss the comments on PCI QSA security assessment report. To be honest, if the classification level of data includes in PCI security requirement. A question you might voice out. What is the responsibilities on payment card industry authority of this incident?
How serious will democracy be concerned about this matter? see below url for reference:
PCI regulations highlights
20,000 to 1 million:
Level 3 Secure a regular network scan by an Approved Scanning Vendor Do an annual Self Assessment Questionnaire Complete an Attestation of Compliance
1 to 6 million:
Level 2 Secure a regular network scan by an Approved Scanning Vendor Do an annual Self Assessment Questionnaire Complete an Attestation of Compliance
6 Million plus:
Level 1 Secure a regular network scan by an Approved Scanning Vendor Have a Qualified Security Assessor do an annual Report on Compliance Complete an Attestation of Compliance