http://img.photobucket.com/albums/v704/chanpicco/chanpicco070/App-dev_zpstuucqzml.jpg
Preface
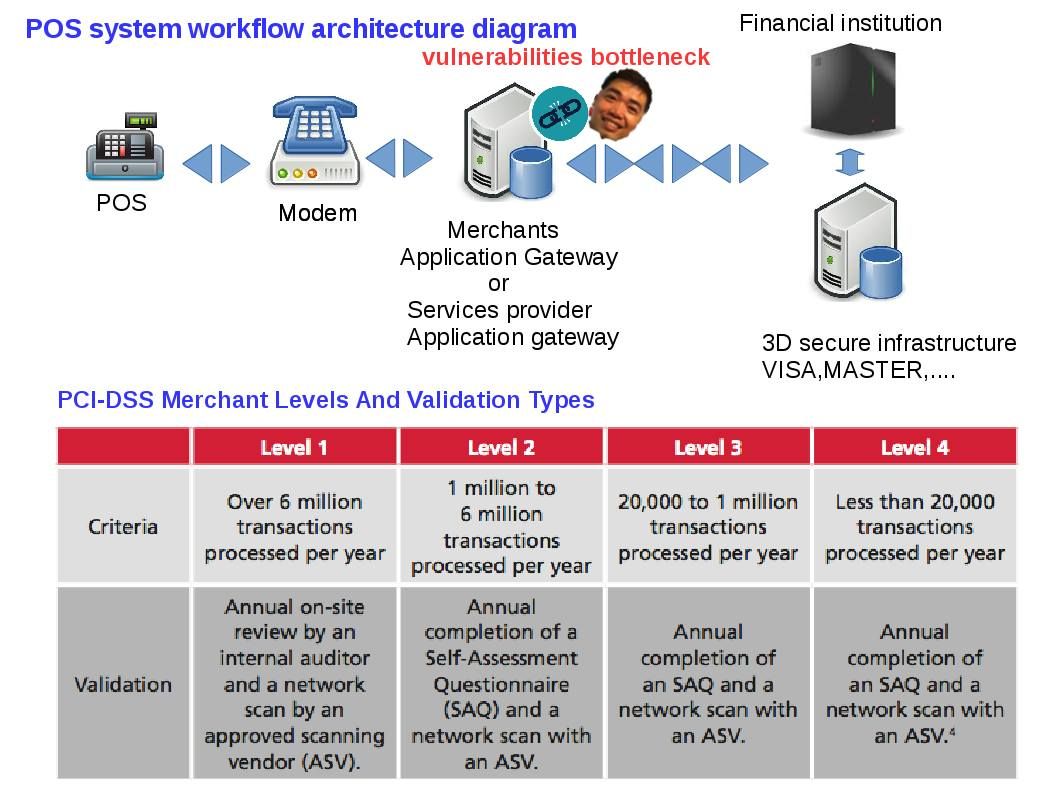
The term BYOD first entered common use in 2009, BYOD conceptual idea looks go to another phase today. The internet of things (IoT) is the network of physical devices, vehicles, buildings and other items—embedded with electronics, software, sensors, actuators, and network connectivity that enable these objects to collect and exchange data. New products and new markets are being rapidly created base on software innovations. On the other hand, it bring out security concerns. This topic is going to provides the fundamental concept. On how, application developers consider those factors (security in technology area).
Application development best practices
1. Avoid to combine new application into existing applications: large legacy software coding that are being reused and modified for current applications.
2. Security considerations : during software design cycle in regards to the buffer overflows, memory leaks, data protection (encryption), and other most common defects (Operating system and programmable interface software).
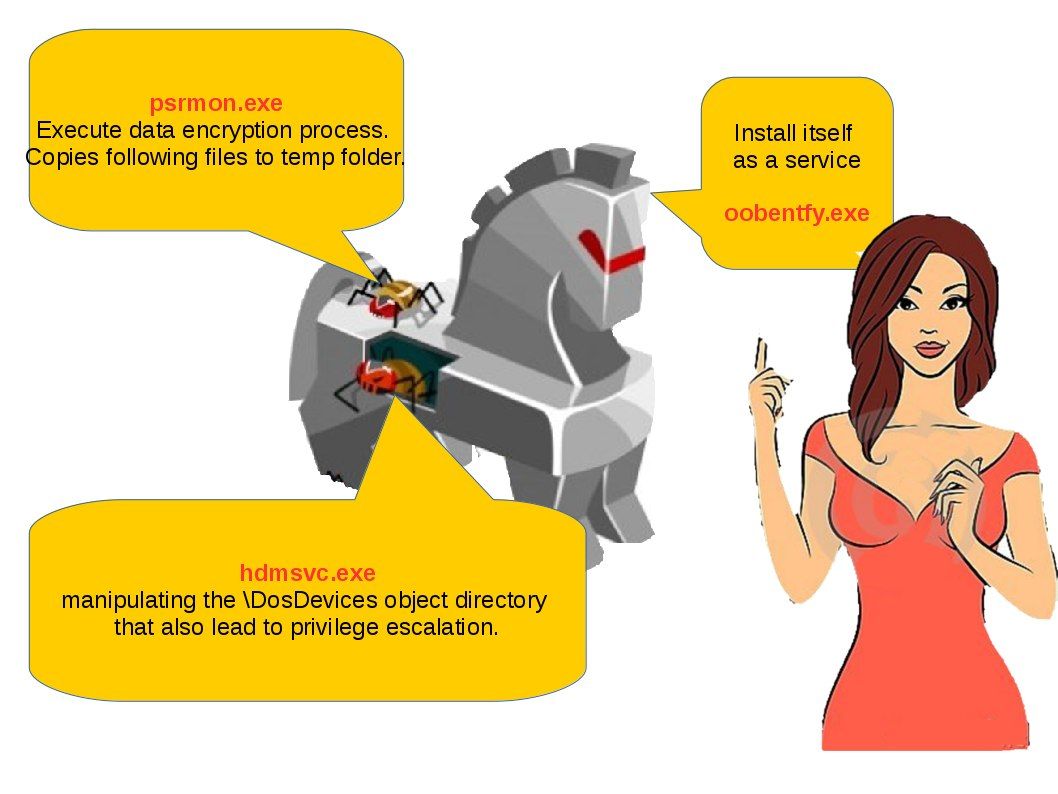
3. Application threat modeling:
- Spoofing – Accessing and using another user’s authentication information.
- Tampering – Alteration of data as it flows over an open network.
- Repudiation – Users denying the performance of an illegal action, in an environment where accountability can’t be identified.
- Information Disclosure – Disclosing of information to individuals without access rights.
- Denial of Service – DoS attacks against valid application users.
- Elevation of Privilege – Unauthorised users gaining privileged access status.
4. Authentication: All authentication attempts should be logged, and repeatedly failed logins should trigger an account lock-out.
5. Access Control (least privilege model) – basic level of data access by default.
6. Input data validation: SQL injection and XSS are two of the most common application vulnerabilities. Define data validation scheme to avoid malicious data input.
7. Application session management: cookies need to be sanitised, and devoid of any sensitive information; and session IDs should be unique to each user, and randomly generated after successful authentication.
Any more, yes. stay tuned!