Preface: In line with its Industrie 4.0 effort, Google Cloud will use the OPC UA open standard to incorporate machine data into analytics and AI solutions.
The existing atmosphere of the Internet world – According to the network attack statistics report. Different types of attacks are involved. Nowadays, receiving personal or confidential data illegally is one of the way run aggressive by attackers. In the future, we foreseen that many vendors will be planned to phase out basic authentication using passwords and cookie-based authentication.
Business needs drive the implementation of new technologies – Integrated with IT. OT-BASE allows IT applications to pull asset information via a powerful REST API. This way you can easily leverage OT asset details in SIEM, data analysis and custom built applications.
Genesis of new concept: Cloud collaboration enables people to work simultaneously on documents that live ‘in the cloud’. Consolidation of OT configuration details in a central platform, accessible by web browser and REST API. System details are no longer known to individual engineers only, but are instantly available to every team member, making the team more efficient.
OPC Unified Architecture (OPC UA) is one of the most important communication protocols for Industry 4.0 and the IoT. Let do a quick review of OPC UA security features.
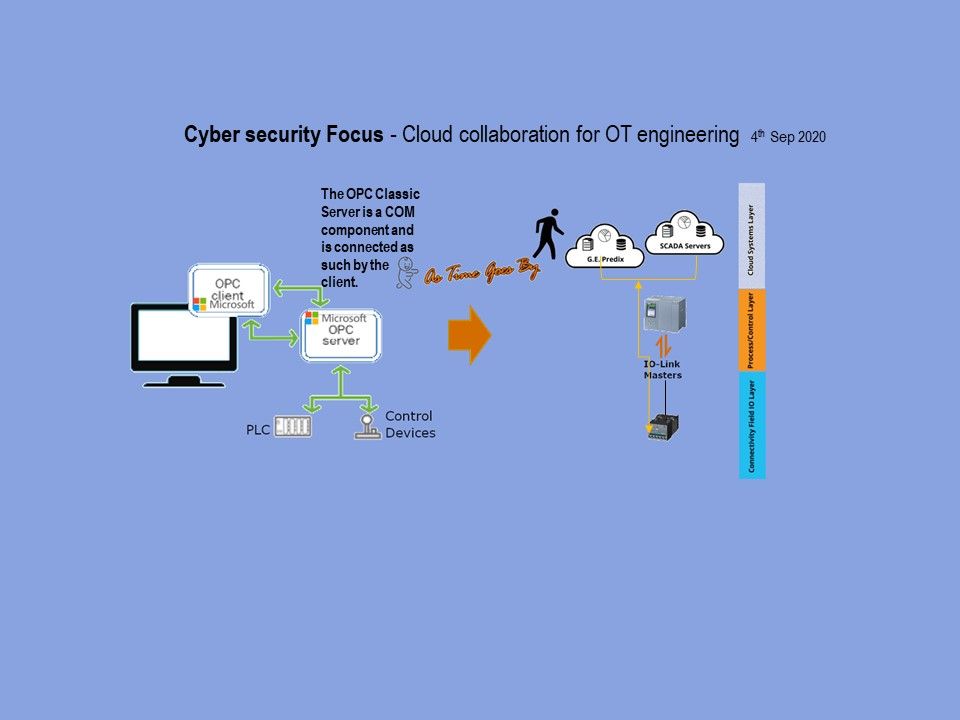
Unlike OPC Classic, OPC UA design is able to working with firewall technology because it support TCP/IP communication protocol. Whereby, it can be managed and governance through standard network technologies.
Remark: OPC Classic using DCOM as a communication protocol. Due to the DCOM technology used, cross-network communication via OPC Classic is very difficult.
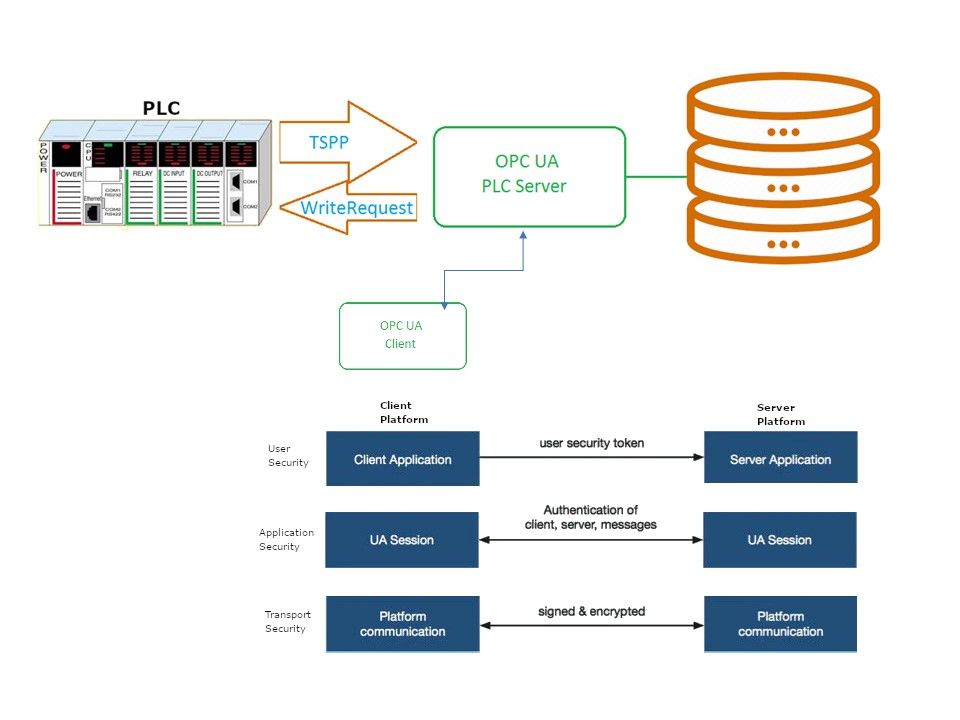
In general practice, the OPC UA software application development will using Simple Object Access Protocol (SOAP). SOAP is a simple XML-based protocol that enables applications to exchange information via HTTP. Meanwhile, OPC UA uses a certificate exchange for further security, so that each client has to authenticate with a certificate. In this way it can be controlled which client is allowed to connect to the server. In the sense that it has access control implement.
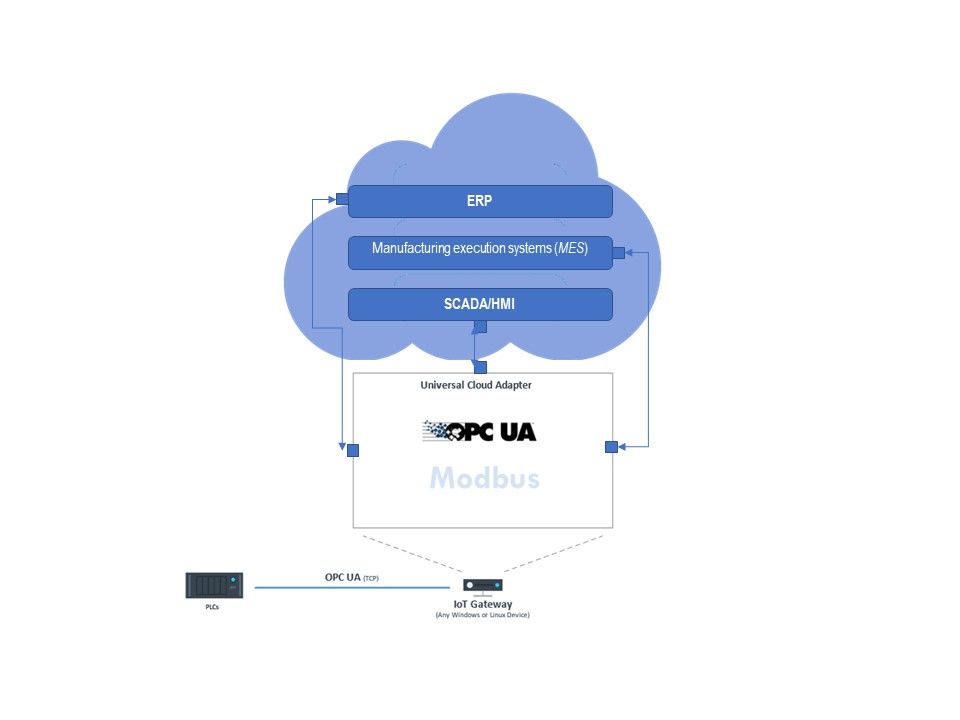
Advanced System Integration – Data exchange between PLC and REST interface
To create or modify objects using data from a PLC, the PLC can be connected via OPC UA and the OPC Client plug-in. Which objects can be addressed in the target system can be queried and browsed via the OpenAPI / Swagger function by the OPC router. If, for example, a batch can be created via REST, the PLC must provide all data in OPC data points when the batch is created and trigger the REST call. The data points are then transferred as a JSON packet by REST call and the batch is created as an object.
Technical Background: REST or RESTful API design (Representational State Transfer) is designed to take advantage of existing protocols. While REST can be used over nearly any protocol, it usually takes advantage of HTTP when used for Web APIs. This means that developers do not need to install libraries or additional software in order to take advantage of a REST API design. It includes four types most-commonly-used HTTP verbs (see below):
- “GET” to retrieve a resource.
- “PUT” to change the state of or update a resource, which can be an object, file or block.
- “POST” to create that resource;
- “DELETE” to remove it.
Additional: “PATCH” applies a partial update to the resource. This means that you are only required to send the data that you want to update, and it won’t affect or change anything else.
Even the flexibility of the design allowed to use a “curl” command. Curl Options shown as below:
–X , –request – The HTTP method to be used.
–i , –include – Include the response headers.
–d , –data – The data to be sent.
–H , –header – Additional header to be sent.
Example: curl https://xxx[.]restapi[.]com/posts?userId=8
Consolidation of OT configuration details in a central platform, accessible by web browser and REST API. System details are no longer known to individual engineers only, but are instantly available to every team member, making the team more efficient.
Security Focus: REST API has emerged as the most versatile and useful web service API. The major trend in data management today is the move toward cloud integration. REST APIs are most commonly used with SaaS (software as a solution) platforms. Fundamentally speaking, REST focuses on the transferability and consumption of data, rather than providing built-in measures to ensure data security during transmission. Perhaps today it has been enhanced using the HTTPS method. But is this enough to prevent today’s cyber attacks? Below list are some of the known cyber attack. Let take a quick look.
- The attacker could be at the client side. Attacker can creates a rogue. It aim to consuming resources from destination server.
- For resources exposed by RESTful web services, attacker can exploit application vulnerability (Cross Site Request Forgery) to execute PUT, POST, and DELETE functions.
- The attack scenario will be according of the architecture set up. If four types most-commonly-used HTTP verbs do not have access control. As a result, the impact will be included server side and related infrastructure.
How to secure industrial communications with OPC UA (see below):
- At least the “Basic256Sha256” security policy should be selected.
- Never store private keys or the corresponding certificate files on an unencrypted file system. Use the dedicated certificate stores of your operating system and use operating system capabilities for setting the access rights.
- Because Java components sometimes find vulnerabilities. Thereby affecting customized Java applications. Therefore, patch and vulnerability management should follow best practices.
Summary: Since HTTPS is suggest to used to call REST endpoints, the authentications available in the standard system can also be used OAuth1 and OAuth2.Besides the standard authentication options, a so-called AppKey is often exchanged. This key is a secret code created for the client, which is transferred with every call to get the authorization for the call. In General point of view, REST is considered secure due to the use of widely used methods.