Preface: The APT organization provides a hard-to-detect malware to attack other hostile campus.
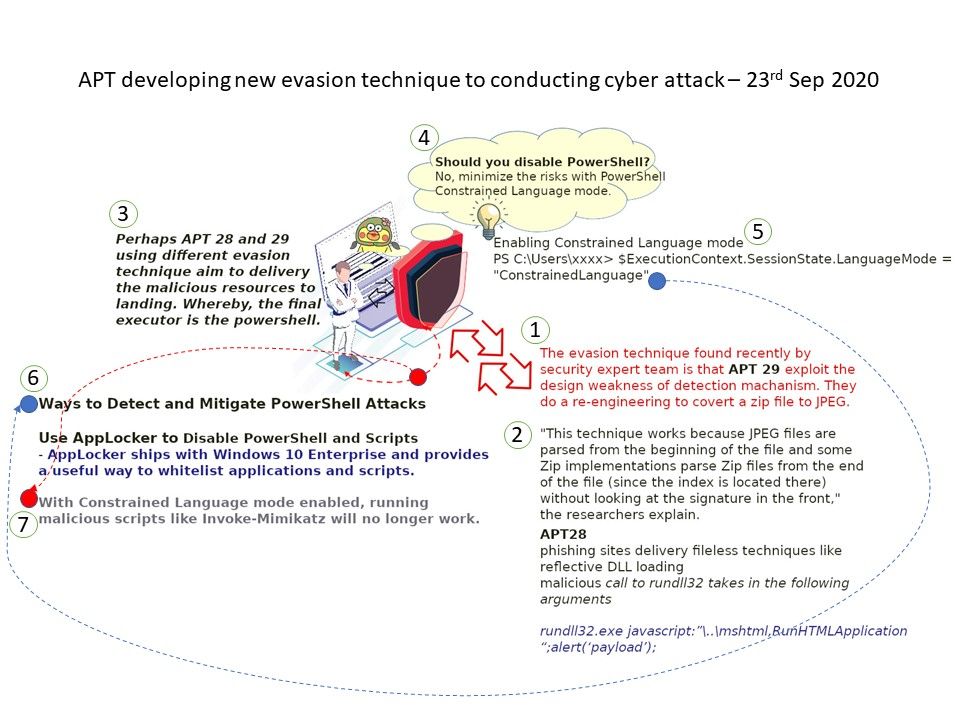
Synopsis: The evasion technique found recently by security expert team is that APT 29 exploit the design weakness of detection machanism. They do a re-engineering to covert a zip file to JPEG.
“This technique works because JPEG files are parsed from the beginning of the file and some Zip implementations parse Zip files from the end of the file (since the index is located there) without looking at the signature in the front,” the researchers explain.
Perhaps APT 28 and 29 using different evasion technique aim to delivery the malicious resources to landing. Whereby, the final executor is the power shell.
So called Zebrocy. Its function is mainly Downloader. The evasion effect is better than the technique use by APT 29. After running, it will perform a persistence operation and pop up an error message box to confuse the user. When it is started with specific parameters, a screenshot will be taken. Through the timer callback function, send data to the remote server and wait for the subsequent payload to be downloaded.
Should you disable PowerShell?
No, minimize the risks with PowerShell Constrained Language mode.
Enabling Constrained Language mode ^
PS C:\Users\xxxx> $ExecutionContext.SessionState.LanguageMode = “ConstrainedLanguage”
This could be configured in registry HKLM\System\CurrentControlSet\Control\SESSION MANAGER\Environment__PSLockdownPolicy .
Running PS as Admin you can simple remove this property
Remove-ItemProperty -path “HKLM:\SYSTEM\CurrentControlSet\Control\Session Manager\Environment\” -name __PSLockdownPolicy
Recommended article: PSLockDownPolicy and PowerShell Constrained Language Mode – https://docs.microsoft.com/en-us/archive/blogs/kfalde/pslockdownpolicy-and-powershell-constrained-language-mode