Preface:
AWS cloud business keep running strong in the market. Amazon S3 or Amazon Simple Storage Service is a “simple storage service” offered by Amazon Web Services (AWS) that provides object storage through a web service interface.
Synopsis:
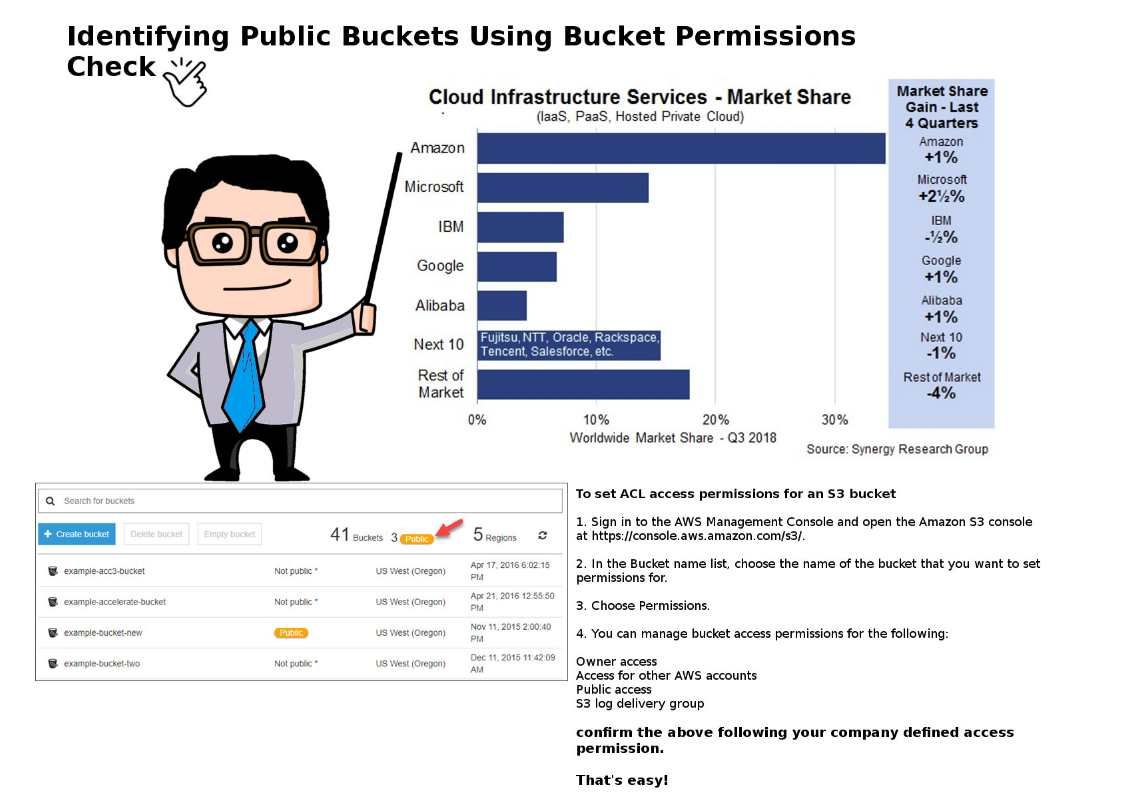
S3 buckets can be configured with public access. But S3 looks like a burden for AWS reputation. Since the access permission is similar do it yourself service type.
So, AWS customer must be confirm the access permission themselves in order to cope with their business function access permission policy.
However if customer apply the services with mistaken permission setup. It will be jeopardizing AWS company reputation as well.
Former records:
Alteryx S3 leak leaves 123m American households exposed1 – Dec 19, 2017
Open AWS S3 bucket exposes private info on thousands of Fedex customers2 – Feb 15, 2018
Sensitive medical records on AWS bucket found to be publicly accessible3 – Jan 22, 2018
Domain Name Registrar was exposed Online (31,000 GoDaddy servers) – Aug 2018
How to avoid?
Hints can find in the following document (Identifying Public Buckets Using Bucket Permissions Check).
https://docs.aws.amazon.com/AmazonS3/latest/user-guide/set-bucket-permissions.html