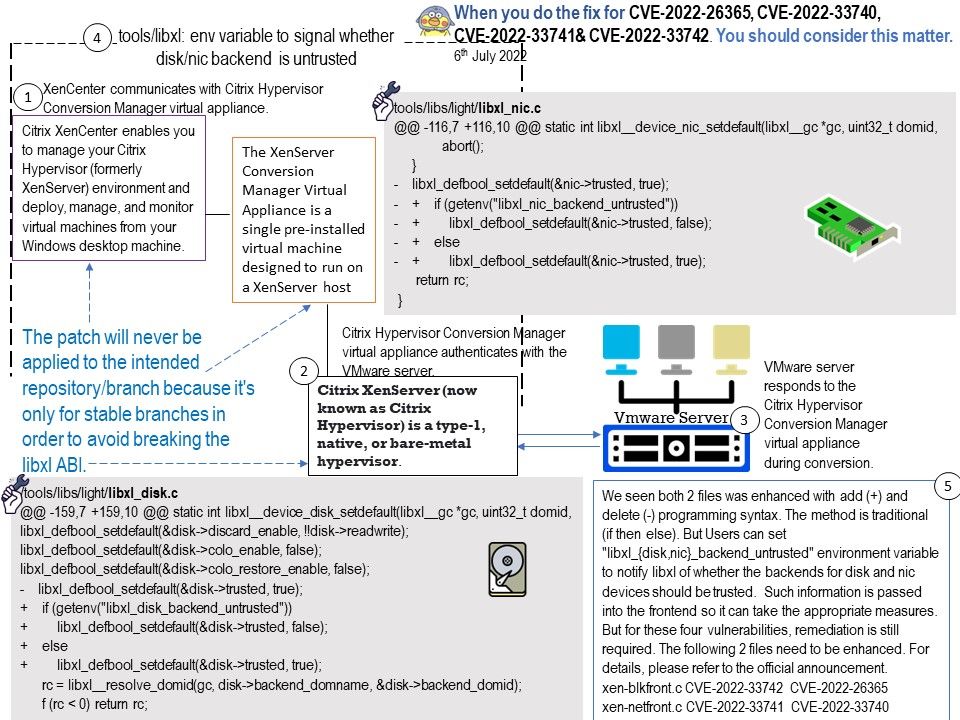
Preface: When you do the fix for CVE-2022-26365, CVE-2022-33740, CVE-2022-33741& CVE-2022-33742. You should consider this matter.
Patch 1 introduces a new field to the disk and nic configurations that allow signaling on a per-device basis whether the backend should be trusted. This is an ABI incompatible change, and cannot be applied to stable branches.
Patch 2 introduces support to libxl for libxl_{disk,nic}_backend_untrusted environment variable to be used in order to set whether disk and network frontends should be trusted in the absence of a per-device setting.
Background:Citrix Hypervisor is based on the Xen Project hypervisor, with extra features and supports provided by Citrix. Citrix XenServer is an open source server virtualization platform based on the Xen hypervisor. Citrix also offers a supported version that you can purchase, with two options: Standard and Enterprise.
Citrix Hypervisor requires at least two separate physical x86 computers: one to be the Citrix Hypervisor server and the other to run the XenCenter application or the Citrix Hypervisor Command-Line Interface (CLI).
Vulnerability details: Linux Block and Network PV device frontends don’t zero memory regions before sharing them with the backend (CVE-2022-26365, CVE-2022-33740). Additionally the granularity of the grant table doesn’t allow sharing less than a 4K page,leading to unrelated data residing in the same 4K page as data shared with a backend being accessible by such backend (CVE-2022-33741, CVE-2022-33742).
The following 2 files need to be enhanced. For details, please refer to the official announcement. Linux disk/nic frontends data leaks – https://xenbits.xen.org/xsa/advisory-403.html
xen-blkfront.c – CVE-2022-33742 CVE-2022-26365
xen-netfront.c – CVE-2022-33741 CVE-2022-33740
IMPACT: An untrusted backend can access data not intended to be shared. If such mappings are made with write permissions the backend could also cause malfunctions and/or crashes to consumers of contiguous data in the shared pages.