Preface: Registering callback in C means you are providing function pointer to any module. When any event arises, registered function will be called to serve this event.
Background: The netfilter hooks are a framework inside the Linux kernel that allows kernel modules to register callback functions at different locations of the Linux network stack. The registered callback function is then called back for every packet that traverses the respective hook within the Linux network stack.
Connction tracking in Linux kernel is implemented as a module in Netfilter framework. Netfilter is a packet manipulating and filtering framework inside the kernel. It provides several hooking points inside the kernel, so packet hooking, filtering and many other processings could be done.
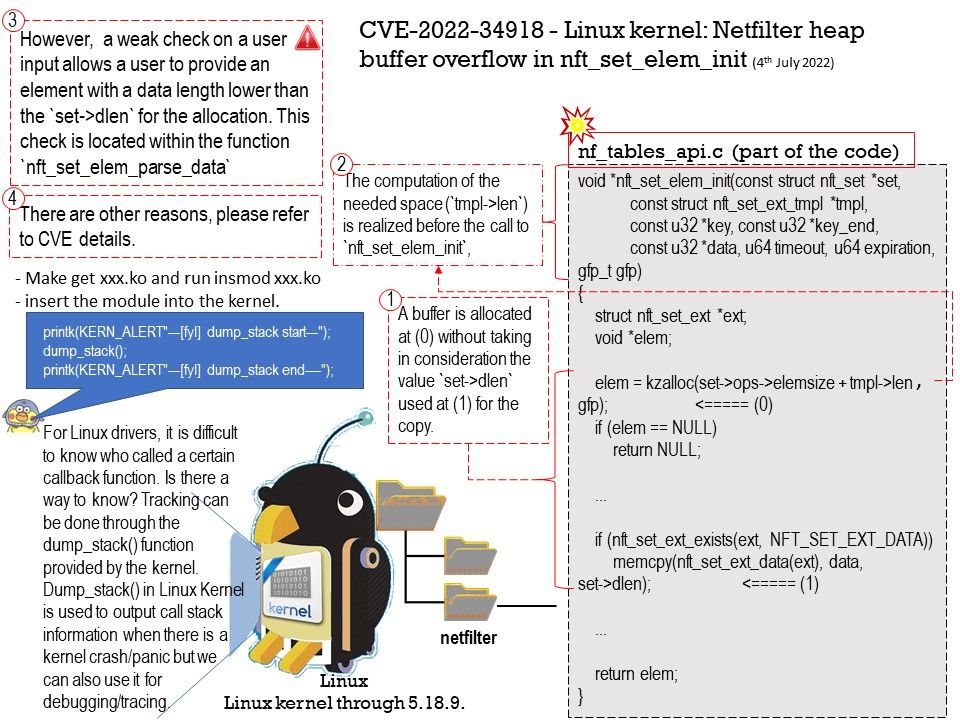
Vulnerability details: An issue was discovered in the Linux kernel through 5.18.9. A type confusion bug in nft_set_elem_init (leading to a buffer overflow) could be used by a local attacker to escalate privileges, a different vulnerability than CVE-2022-32250. (The attacker can obtain root access, but must start with an unprivileged user namespace to obtain CAP_NET_ADMIN access.)
Ref: The user namespace is a way for a container (a set of isolated processes) to have a different set of permissions than the system itself. Every container inherits its permissions from the user who created the new user namespace. For example, in most Linux systems, regular user IDs start at or above 1000.
Remedy: This can be fixed in nft_setelem_parse_data in net/netfilter/nf_tables_api[.]c. For details please refer to link – https://git.kernel.org/pub/scm/linux/kernel/git/netdev/net.git/commit/?id=7e6bc1f6cabcd30aba0b11219d8e01b952eacbb6
Additional information: For Linux drivers, it is difficult to know who called a certain callback function. Is there a way to know? Tracking can be done through the dump_stack() function provided by the kernel. Dump_stack() in Linux Kernel is used to output call stack information when there is a kernel crash/panic but we can also use it for debugging/tracing.