Preface: TCP / IP design restrictions have introduced security vulnerabilities to transport protocols.
Security focus: Memory leak vulnerability in VMCI module (CVE-2020-3959) – VMware ESXi, Workstation and Fusion contain a memory leak vulnerability in the VMCI module. It lets local non-administrative user send a malformed packet to a virtual machine. Such action may be able to crash the virtual machine’s vmx process leading to a partial denial of service.
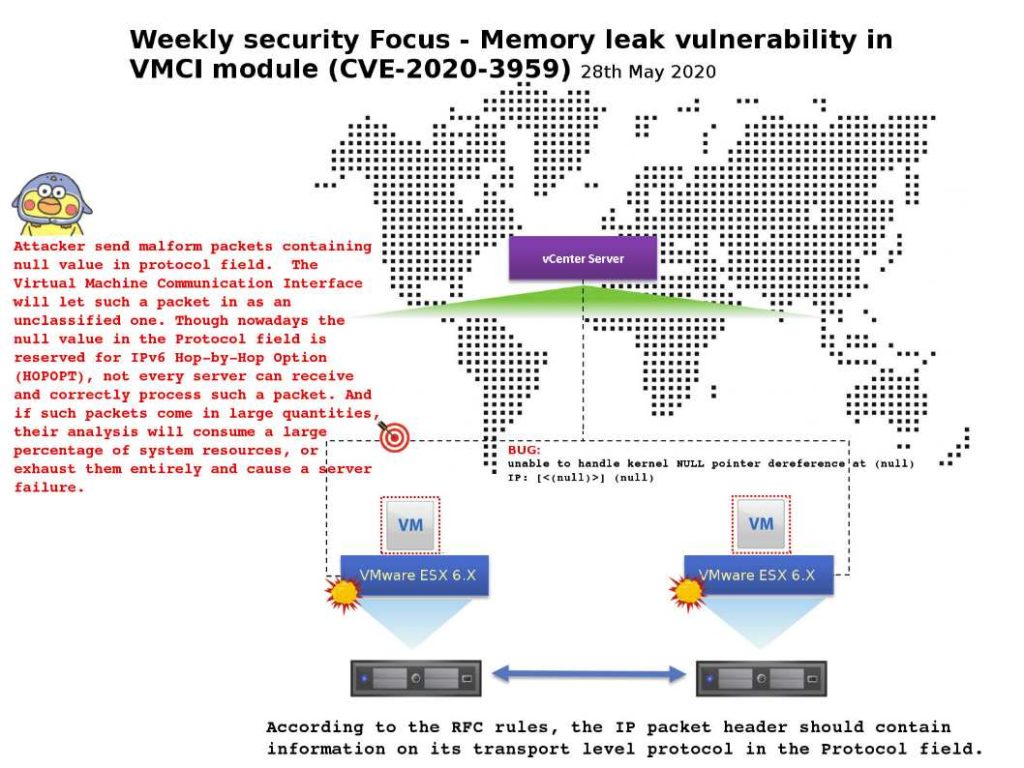
Possible root cause: Attacker send malform packets containing null value in protocol field. The Virtual Machine Communication Interface will let such a packet in as an unclassified one. Though nowadays the null value in the Protocol field is reserved for IPv6 Hop-by-Hop Option (HOPOPT), not every server can receive and correctly process such a packet. And if such packets come in large quantities, their analysis will consume a large percentage of system resources, or exhaust them entirely and cause a server failure.
Remark: According to the RFC rules, the IP packet header should contain information on its transport level protocol in the Protocol field.
Official details please find follow link: https://www.vmware.com/security/advisories/VMSA-2020-0011.html