Preface: VMware has released a security update on August 24, 2021 to address vulnerabilities in multiple products. In addition, the risk level of these vulnerabilities is between 4.4-8.6 (CVSS-V3). So it attracted my interest in reading it.
Background: The vRealize Operations Manager API Programming Guide provides information about the vRealize Operations Manager REST APIs, including how to use the REST API resources, authenticate, and construct REST API calls.
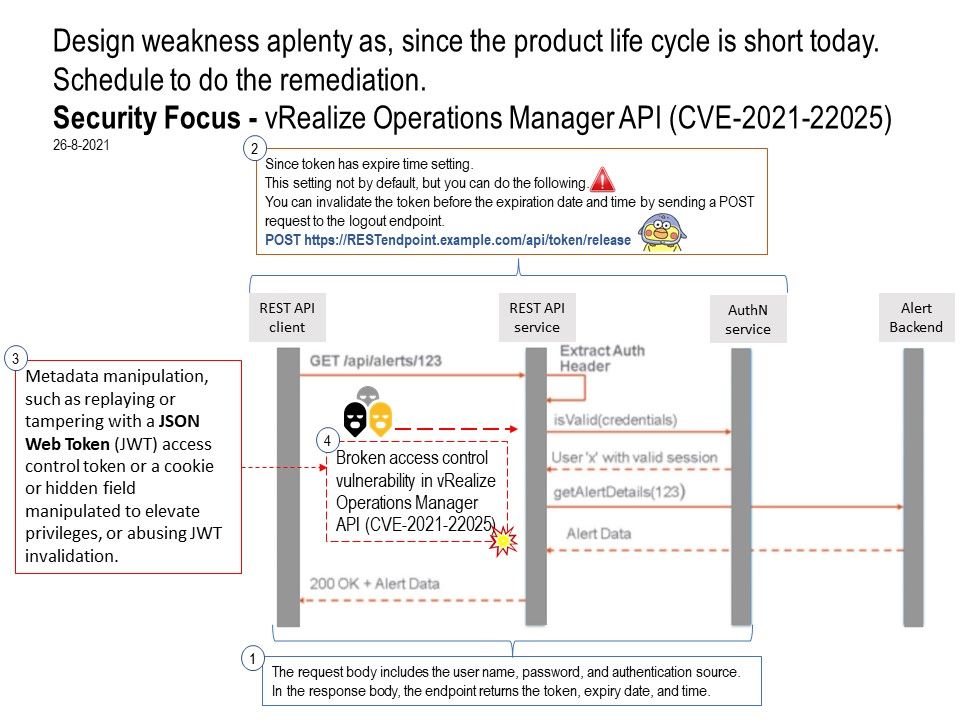
Our focus on this time is (CVE-2021-22025). The flaw is that it allow an unauthenticated malicious actor with network access to the vRealize Operations Manager API. the risk rating is CVSSv3 base score of 8.6. Furthermore the article mentioned that it can add new nodes to existing vROps cluster when hack successful. Per my idea, all depends on the token type capture by attacker. If it is a privileges user, the access permission is high.
Remark: vROps_token is the token that you obtained from the response in Acquire an Authentication Token
Meanwhile, VMware programming guide had below function ready.
Since token has expire time setting. This setting not by default, but you can do the following. You can invalidate the token before the expiration date and time by sending a POST request to the logout endpoint. For details, please refer to attached diagram for reference.
Vulnerability summary:
Broken access control vulnerability in vRealize Operations Manager API (CVE-2021-22025) – CVSSv3 base score of 8.6.
Arbitrary log-file read vulnerability in vRealize Operations Manager API (CVE-2021-22024) – CVSSv3 base score of 7.5.
Server Side Request Forgery in vRealize Operations Manager API (CVE-2021-22026, CVE-2021-22027) – CVSSv3 base score of 7.5.
Insecure direct object reference vulnerability in vRealize Operations Manager API (CVE-2021-22023) – CVSSv3 base score of 6.6.
Arbitrary file read vulnerability in vRealize Operations Manager API (CVE-2021-22022) – CVSSv3 base score of 4.4.
Official announcement (Remediation) – https://www.vmware.com/security/advisories/VMSA-2021-0018.html