Preface: Today developers are using Docker to build modules called Microservices, which decentralize packages and divide tasks into separate, stand-alone apps that collaborate with each other.
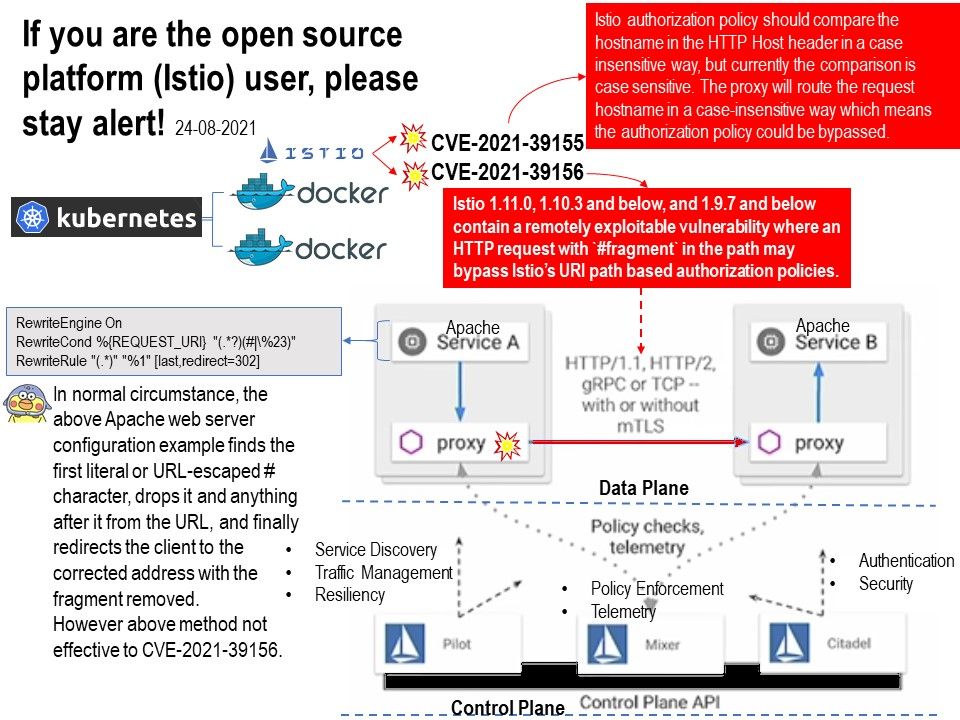
Background: A sidecar proxy is an application design pattern which abstracts certain features, such as inter-service communications, monitoring and security, away from the main architecture to ease the tracking and maintenance of the application as a whole. Furthermore, the sidecar proxy for each application has all the non-business logic. So, it lets developers can focus on application/service itself not worring about security or monitoring etc. Istio has two components: the data plane and the control plane. The data plane is the communication between services. And the control plane takes your desired configuration, and its view of the services, and dynamically programs the proxy servers, updating them as the rules or the environment changes.
Vulnerability details:
CVE-2021-39156: Istio 1.11.0, 1.10.3 and below, and 1.9.7 and below contain a remotely exploitable vulnerability where an HTTP request with `#fragment` in the path may bypass Istio’s URI path based authorization policies.
Remedy: Patches are available in Istio 1.11.1, Istio 1.10.4 and Istio 1.9.8.
CVE-2021-39155: Istio authorization policy should compare the hostname in the HTTP Host header in a case insensitive way, but currently the comparison is case sensitive. The proxy will route the request hostname in a case-insensitive way which means the authorization policy could be bypassed.
Remedy: Patches are available in Istio 1.11.1, Istio 1.10.4 and Istio 1.9.8.