Preface: In some languages such as C and C++, stack variables are not initialized by default. They generally contain junk data with the contents of stack memory before the function was invoked. An attacker can sometimes control or read these contents.
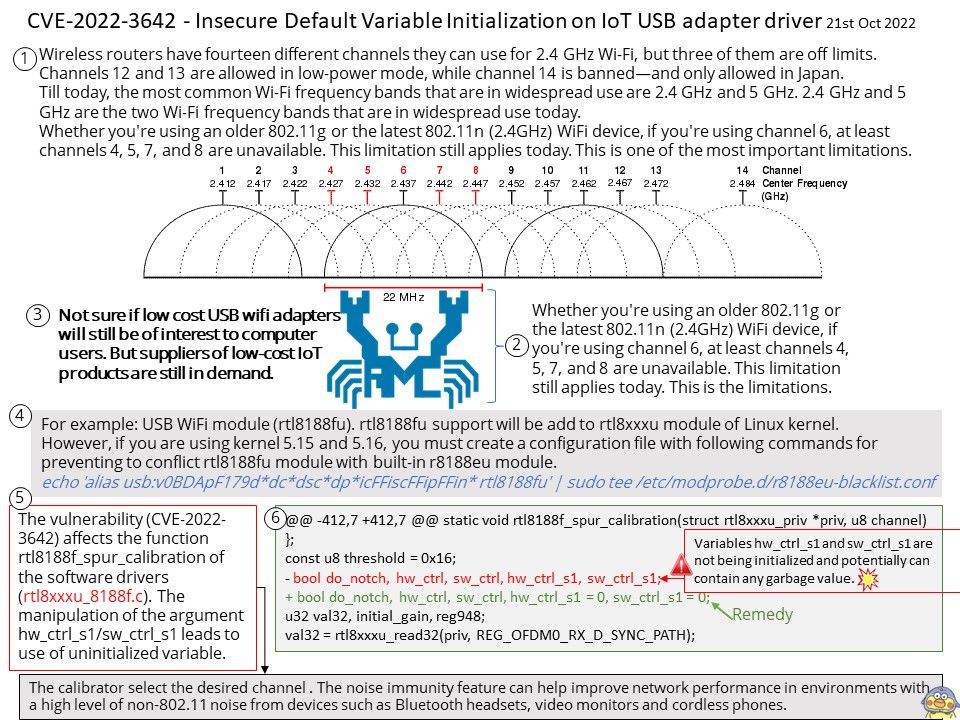
Background: Wireless routers have fourteen different channels they can use for 2.4 GHz Wi-Fi, but three of them are off limits. Channels 12 and 13 are allowed in low-power mode, while channel 14 is banned—and only allowed in Japan.
Till today, the most common Wi-Fi frequency bands that are in widespread use are 2.4 GHz and 5 GHz. 2.4 GHz and 5 GHz are the two Wi-Fi frequency bands that are in widespread use today.
Not sure if low cost USB wifi adapters will still be of interest to computer users. But suppliers of low-cost IoT products are still in demand.
For example: USB WiFi module (rtl8188fu). rtl8188fu support will be add to rtl8xxxu module of Linux kernel.
However, if you are using kernel 5.15 and 5.16, you must create a configuration file with following commands for preventing to conflict rtl8188fu module with built-in r8188eu module.
echo ‘alias usb:v0BDApF179ddcdscdpicFFiscFFipFFin* rtl8188fu’ | sudo tee /etc/modprobe.d/r8188eu-blacklist[.]conf
Vulnerability details: A vulnerability classified as problematic has been found in Linux Kernel. This affects the function rtl8188f_spur_calibration of the file drivers/net/wireless/realtek/rtl8xxxu/rtl8xxxu_8188f[.]c of the component Wireless. The manipulation of the argument hw_ctrl_s1/sw_ctrl_s1 leads to use of uninitialized variable. It is recommended to apply a patch to fix this issue.
Please refer to the link for details – https://git.kernel.org/pub/scm/linux/kernel/git/wireless/wireless-next.git/commit/?id=80e5acb6dd72b25a6e6527443b9e9c1c3a7bcef6