Preface: One time password is secure. What If we following their algorithm generate a password and apply in both end. If it is matches with each other. Can we do the exploit? Perhaps the answer is “Yes”. The key technology is you understand how to use the “Time” value.
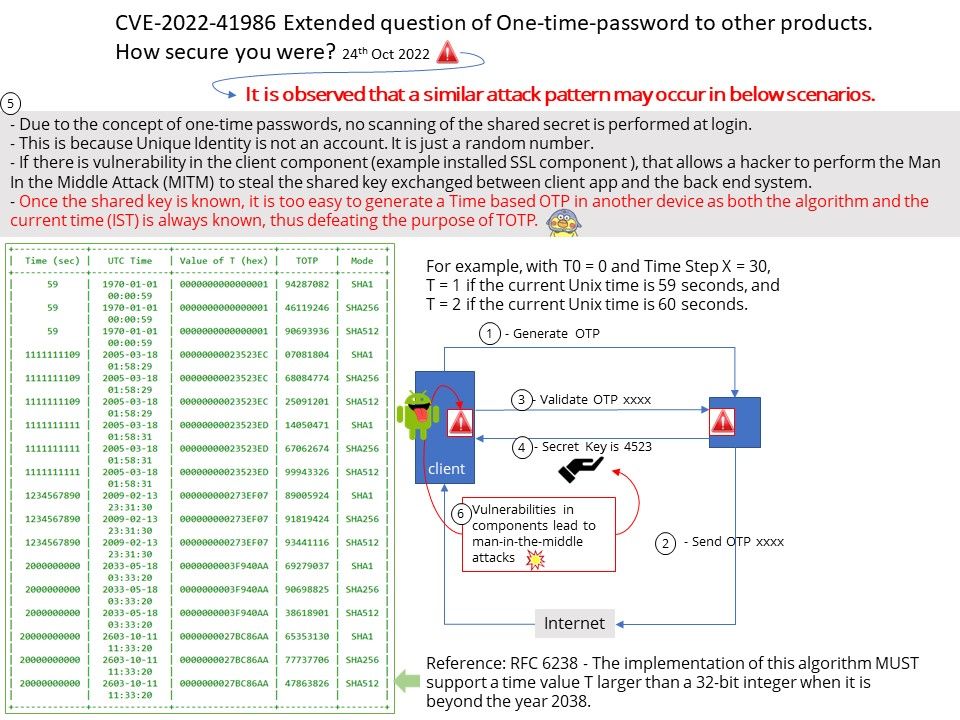
Background: The IIJ SmartKey app produces one-time passwords that conform to TOTP (RFC 6238) standards and can be used in the 2-step verification authentication processes of a variety of online services supporting TOTP. RFC 6238 – The implementation of this algorithm MUST support a time value T larger than a 32-bit integer when it is beyond the year 2038.
The HMAC-based One-Time Password (HOTP) algorithm specifies an event-based OTP algorithm, where the moving factor is an event counter. The present work bases the moving factor on a time value. A time-based variant of the OTP algorithm provides short-lived OTP values, which are desirable for enhanced security.
Vulnerability details: A vulnerability, which was classified as problematic, was found in Iij SmartKey up to 2.1.3 on Android (Android App Software). This affects some unknown processing of the component One-Time Password Handler. The manipulation with an unknown input leads to a information disclosure vulnerability. CWE is classifying the issue as CWE-200. The product exposes sensitive information to an actor that is not explicitly authorized to have access to that information. This is going to have an impact on confidentiality. The summary by CVE is:
Information disclosure vulnerability in Android App ‘IIJ SmartKey’ versions prior to 2.1.4 allows an attacker to obtain a one-time password issued by the product under certain conditions.
Official description: This vulnerability was fixed in version 2.1.4 released on June 16, 2020. Please refer to the link for details – https://jvn.jp/en/jp/JVN74534998/index.html
Remedy: Upgrading to version 2.1.4 eliminates this vulnerability.
10/07/2022 CVE reserved
10/24/2022 +17 days Advisory disclosed