Preface: The REP MOVSB/STOSB instruction can enhance fast strings attempts to move as much of the data with larger size load/stores as possible. So, a patch exposes ERMS feature to KVM guests in June 2011.
Background: REP is a prefix that makes the processor repeat the following instruction. It decrements the RCX register each time the following instruction is executed until RCX reaches zero. REP MOVSB assembles to just two bytes of machine code, ‘F3’ and ‘A4’ in hex, so it’s an incredibly concise way of doing a data copy.
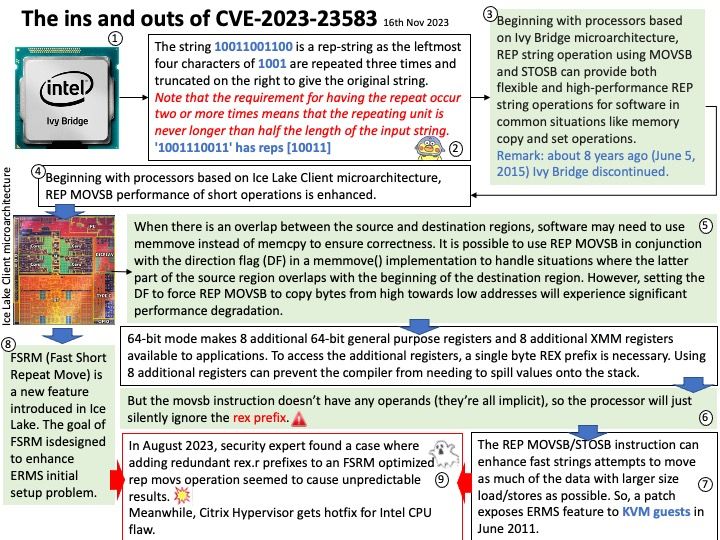
When there is an overlap between the source and destination regions, software may need to use memmove instead of memcpy to ensure correctness. It is possible to use REP MOVSB in conjunction with the direction flag (DF) in a memmove() implementation to handle situations where the latter part of the source region overlaps with the beginning of the destination region. However, setting the DF to force REP MOVSB to copy bytes from high towards low addresses will experience significant performance degradation.
Ref: What is the purpose of the direction flag? This flag is used to determine the direction (‘forward’ or ‘backward’) in which several bytes of data will be copied from one place in the memory, to another. The direction is important mainly when the original data position in memory and the target data position overlap.
Vulnerability details: Under certain microarchitectural conditions, Intel has identified cases where execution of an instruction (REP MOVSB) encoded with a redundant REX prefix may result in unpredictable system behavior resulting in a system crash/hang, or, in some limited scenarios, may allow escalation of privilege from CPL3 to CPL0.
Remediation: Intel is providing a microcode update to mitigate this issuehttps://github.com/intel/Intel-Linux-Processor-Microcode-Data-Files/releases/tag/microcode-20231114
Official details: Please refer to the link for details –
https://nvd.nist.gov/vuln/detail/CVE-2023-23583
https://www.intel.com/content/www/us/en/security-center/advisory/intel-sa-00950.html
Citrix Hypervisor Security Bulletin for CVE-2023-23583 and CVE-2023-46835 – https://support.citrix.com/article/CTX583037/citrix-hypervisor-security-bulletin-for-cve202323583-and-cve202346835