Preface: As a PostgreSQL database’s workload increases, the instance’s memory usage increases. Instances that consume lots of memory can create a performance bottleneck that can sometimes lead to out-of-memory issues. An integer overflow occurs when you attempt to store inside an integer variable a value that is larger than the maximum value the variable can hold. The C standard defines this situation as undefined behavior. Refer to posgreSQL manual, user-defined functions can be written in C (or a language that can be made compatible with C, such as C++).
Background: PostgreSQL is a powerful, open source object-relational database system. Besides, PostgreSQL is a relational database. It stores data points in rows, with columns as different data attributes. A table stores multiple related rows.
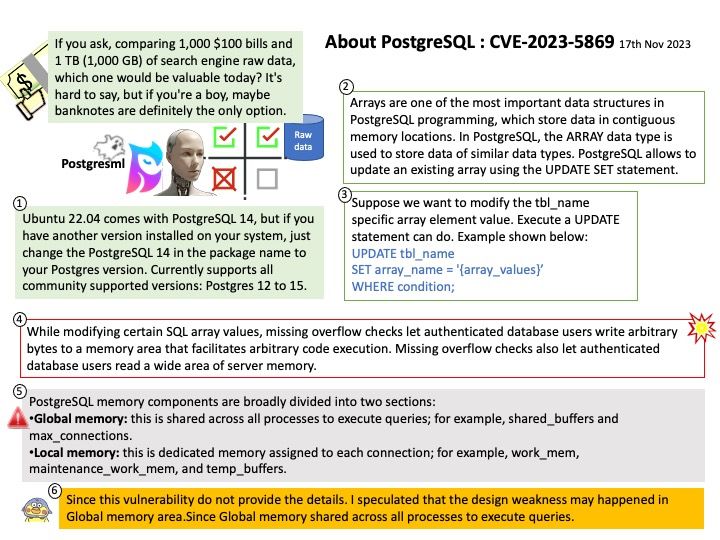
PostgreSQL memory components are broadly divided into two sections:
1.Global memory: this is shared across all processes to execute queries; for example, shared_buffers and max_connections.
2.Local memory: this is dedicated memory assigned to each connection; for example, work_mem, maintenance_work_mem, and temp_buffers.
Vulnerability details: While modifying certain SQL array values, missing overflow checks let authenticated database users write arbitrary bytes to a memory area that facilitates arbitrary code execution. Missing overflow checks also let authenticated database users read a wide area of server memory. The CVE-2021-32027 fix covered some attacks of this description, but it missed others.
About CVE-2021-32027: A flaw was found in postgresql. While modifying certain SQL array values, missing bounds checks let authenticated database users write arbitrary bytes to a wide area of server memory. The highest threat from this vulnerability is to data confidentiality and integrity as well as system availability.
Fixed In Version: PostgreSQL 16.1, PostgreSQL 15.5, PostgreSQL 14.10, PostgreSQL 13.13, PostgreSQL 12.17 and PostgreSQL 11.22
Official announcement: Official details: Please refer to the link for details –
https://www.postgresql.org/about/news/postgresql-161-155-1410-1313-1217-and-1122-released-2749/