Preface: What’s interesting about our focus on CVE-2022-25718 and CVE-2022-25748 is that it exposes weaknesses in the traditional design process. What is closed-source components?
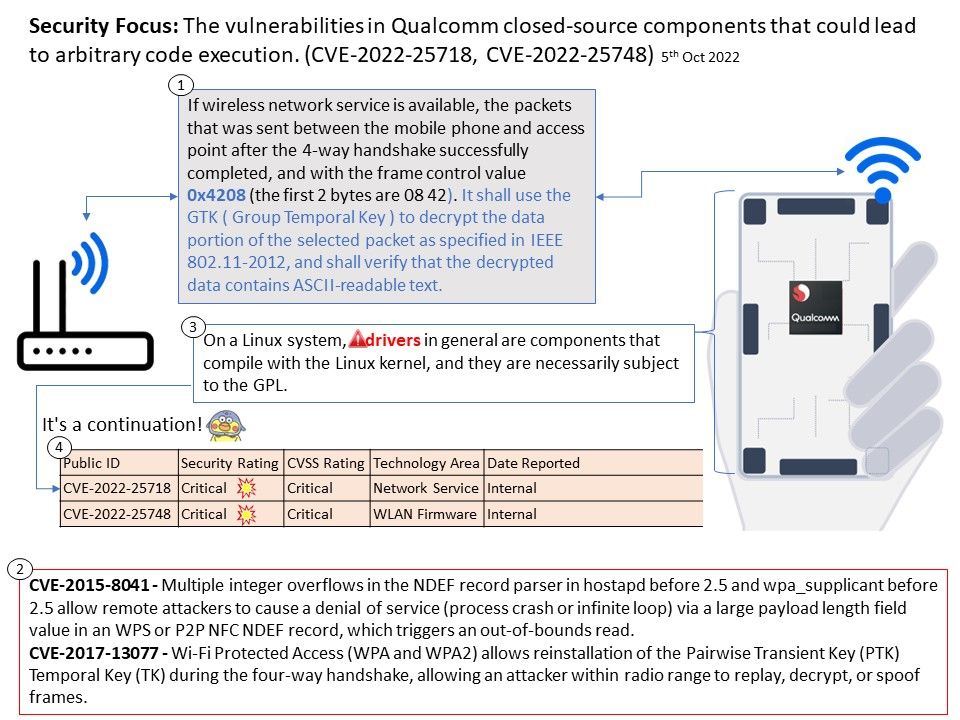
On a Linux system, drivers in general are components that compile with the Linux kernel, and they are necessarily subject to the GPL.
Background and vulnerabilities: IEEE 802.11 standard, popularly known as WiFi, lays down the architecture and specifications of wireless LANs (WLANs).The following are the key factors that trigger these two vulnerabilities.The 4-way handshake frames (denoted EAPOL-key in Wireshark captures) and derive the PTK and GTK from the 4-way handshake frames and pre-shared key as specified in IEEE 802.11-2012.
If wireless network service is available, the packets that was sent between the mobilephone and access point after the 4-way handshake successfully completed, and with the frame control value 0x4208 (the first 2 bytes are 08 42). It shall use the GTK ( Group Temporal Key ) to decrypt the data portion of the selected packet as specified in IEEE 802.11-2012, and shall verify that the decrypted data contains ASCII-readable text.
In 2015, Multiple integer overflows in the NDEF record parser in hostapd before 2.5 and wpa_supplicant before 2.5 allow remote attackers to cause a denial of service (process crash or infinite loop) via a large payload length field value in an (1) WPS or (2) P2P NFC NDEF record, which triggers an out-of-bounds read (CVE-2015-8041).
In October 2017, a design weakness was discovered where an attacker can exploiting client or Access point that could reinstall specific keys (PTK, GTK, IGTK). Key Reinstallation Attack is an attack against the Wi-Fi Protected Access (WPA2) protocol that protects Wi-Fi connections, discovered in 2017 by Belgian researchers Mathy Vanhoef and Frank Piessens of the University of Leuven.
On a Linux system, drivers in general are components that compile with the Linux kernel, and they are necessarily subject to the GPL.
Only Qualcomm can provide security updates for blobs (Binary Large Object), so no OEM can guarantee the security of a phone if Qualcomm doesn’t push security updates. Sure, they could update other components, but it would be frustrating if someone found out that a driver bug could allow for privilege escalation. It is a continuation!
CVE-2022-25748 – Memory corruption in WLAN due to integer overflow to buffer overflow while parsing GTK frames.
CVE-2022-25718 – Cryptographic issue in WLAN due to improper check on return value while authentication handshake
Official announcement: Please refer to the link for details – https://docs.qualcomm.com/product/publicresources/securitybulletin/october-2022-bulletin.html