Preface: By integrating the chip inside future Intel, AMD and Qualcomm central processor units, or CPUs, it makes it far more difficult for hackers with physical access to a computer to launch hardware attacks and extract sensitive data, Microsoft said.
Pluton Security Processor can emulate TPM using APIs, making the integration seamless, thus basically removing the need for TPM. So, for example, encryption keys, user profiles, users’ identities, credentials, etc., can all be secured by Pluton now.
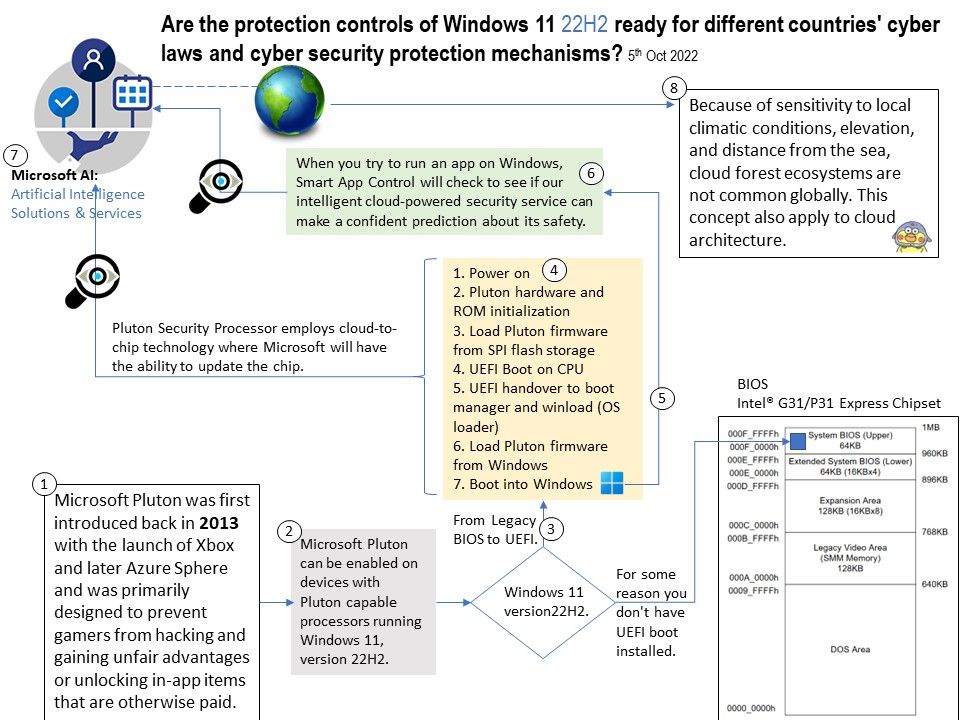
Background: UEFI and BIOS are two different types of motherboard firmware. UEFI replaces the traditional BIOS on PCs. There’s no way to switch from BIOS to UEFI on an existing PC. You need to buy new hardware that supports and includes UEFI, as most new computers do.
The new features for Windows 11 22H2 will be capable to the following features.
- Pluton Security Processor employs cloud-to-chip technology where Microsoft will have the ability to update the chip.
- When you try to run an app on Windows, Smart App Control will check to see if our intelligent cloud-powered security service can make a confident prediction about its safety.
Reminder: Disable BitLocker protection before starting the conversion process. With BitLocker protection turned on, Windows cannot convert your drive from Legacy BIOS to UEFI.
- By pressing Win + X.
- Go to “Shut down or sign out” and click on the “Restart” button while holding the Shift key.
- Go to “Troubleshoot -> Advanced Options” and select the option “Command Prompt.”
- Type command: mbr2gpt /validate and press Enter
If you see the “Validation completed successfully” message, proceed to the next step. - After validating the disk, execute the command: mbr2gpt /convert
- Restart your system, launch your motherboard firmware settings screen and change it from legacy BIOS to UEFI.
Example: Hot keys to access the motherboard firmware.
- Dell: F2 or F12.
- HP: ESC or F10.
- Acer: F2 or Delete.
- ASUS: F2 or Delete.
- Lenovo: F1 or F2.
- MSI: Delete.
- Toshiba: F2.
- Samsung: F2.
- Surface: Press and hold volume up button.
7. After booting into Windows, the above conversion is complete.
About the title – Are the protection controls of Windows 11 22H2 ready for different countries’ cyber laws and cyber security protection mechanisms?
Compared to the hot topic, businesses face privacy laws in global regions. But the situation will be bigger for cybersecurity service providers than for enterprise companies. Since cybersecurity vendors track millions of IoT and/or a huge number of computers. In fact. It is equal to one million nodes. Also, they are located in different areas. As a result, technological gaps are encountered between cyber laws or data protection regulations in different countries.
Therefore, traditional cloud area distribution may not be effective for classification of data. So, this has to rely on the AI architecture. According to technical details provided by Microsoft, the overall operation will be handled by AI mechanisms running on top of its cloud architecture.
Some people, including me, worry that AI will manipulate the world. With the digital age approaching, the use of artificial intelligence technology is inevitable. Maybe this is the reality.