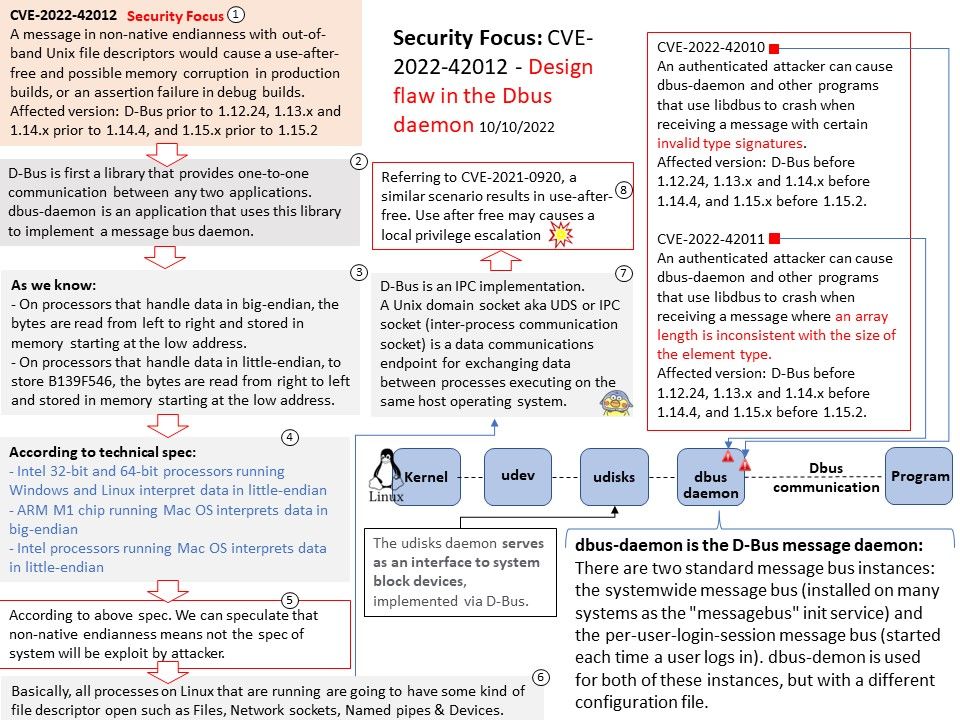
Preface: D-bus has nothing to do with the kernel or the driver, but no one is preventing drivers from having a D-Bus service too, if that’s their design. There are two standard message bus instances: the systemwide message bus (installed on many systems as the “messagebus” init service) and the per-user-login-session message bus (started each time a user logs in). dbus-demon is used for both of these instances, but with a different configuration file.
Background: Endianness means that the bytes in computer memory are read in a certain order.
Big-endian is an order in which the “big end” (most significant value in the sequence) is stored first, at the lowest storage address. Little-endian is an order in which the “little end” (least significant value in the sequence) is stored first.
As we know:
- On processors that handle data in big-endian, the bytes are read from left to right and stored in memory starting at the low address.
- On processors that handle data in little-endian, to store B139F546, the bytes are read from right to left and stored in memory starting at the low address.
Technical spec:
- Intel 32-bit and 64-bit processors running Windows and Linux interpret data in little-endian
- ARM M1 chip running Mac OS interprets data in big-endian
- Intel processors running Mac OS interprets data in little-endian
Vulnerability details:
CVE-2022-42010 – An authenticated attacker can cause dbus-daemon and other programs that use libdbus to crash when receiving a message with certain invalid type signatures.
Impact version: D-Bus before 1.12.24, 1.13.x and 1.14.x before 1.14.4, and 1.15.x before 1.15.2.
https://www.suse.com/security/cve/CVE-2022-42010.html
CVE-2022-42011 – An authenticated attacker can cause dbus-daemon and other programs that use libdbus to crash when receiving a message where an array length is inconsistent with the size of the element type.
Impact version: D-Bus before 1.12.24, 1.13.x and 1.14.x before 1.14.4, and 1.15.x before 1.15.2.
https://gitlab.freedesktop.org/dbus/dbus/-/issues/413
CVE-2022-42012 – A message in non-native endianness with out-of-band Unix file descriptors would cause a use-after-free and possible memory corruption in production builds, or an assertion failure in debug builds.
Remark: For my speculation about this vulnerability, please refer to the attached diagram.
Affected version: D-Bus prior to 1.12.24, 1.13.x and 1.14.x prior to 1.14.4, and 1.15.x prior to 1.15.2
https://ubuntu.com/security/CVE-2022-42012