Preface: Memory is managed differently depending on the programming language in which the application is written. Some languages, such as C, require the programmer to manage direct allocation of memory.
Background: There is usually a requirement in the kernel to find all VMAs that map this page through the struct page data structure. Early linux kernel implementations scan the VMA of all processes, which is quite time consuming. During the development of linux 2.5, the concept of reverse mapping has been formed, and the current version has been formed after years of optimization.
The focus of the vulnerability – Found that virtual memory regions can be reused in the following situations.
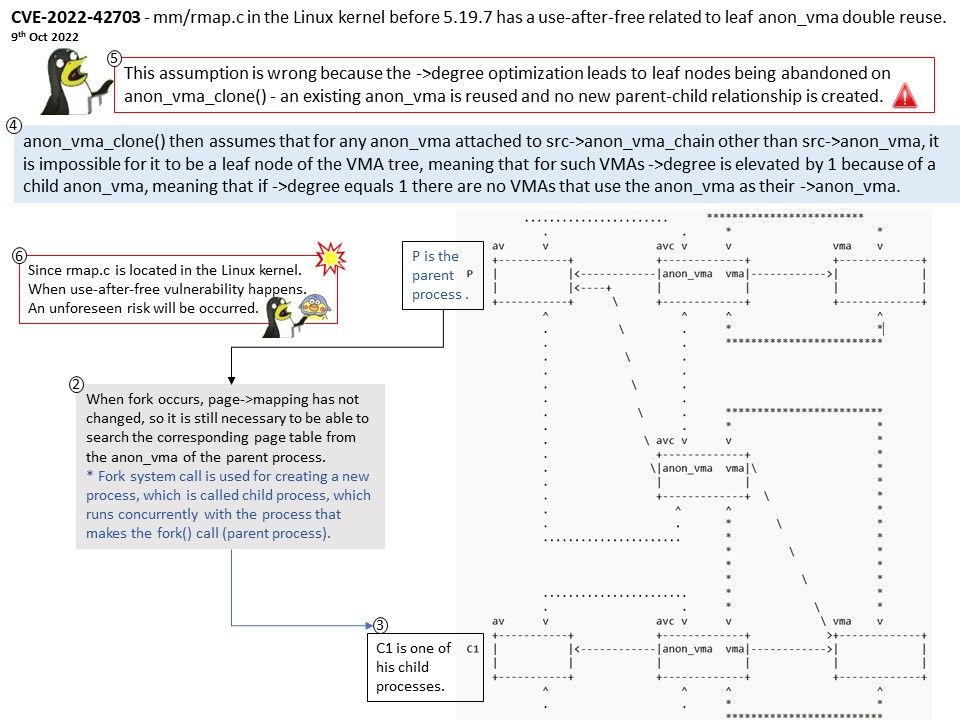
Degree optimization leads to leaf nodes being abandoned on anon_vma_clone() – an existing anon_vma is reused and no new parent-child relationship is created. This assumption is wrong because the ->degree optimization leads to leaf nodes being abandoned on anon_vma_clone() – an existing anon_vma is reused and no new parent-child relationship is created.
Since rmap[.]c is located in the Linux kernel. When use-after-free vulnerability happens. A unforeseen risk will be occurred.
Official details: Please refer to this external link – https://www.tenable.com/cve/CVE-2022-42703
Remedy: Upgrading to version 5[.]19[.]7 eliminates this vulnerability.