Preface: What is the difference of APT group and so called cyber attacker? In normal circumstance, the attack of APT group more often target different political factor of countries or benefits.
Background: Physicists and engineers at CERN use the world’s largest and most complex scientific instruments to study the basic constituents of matter.
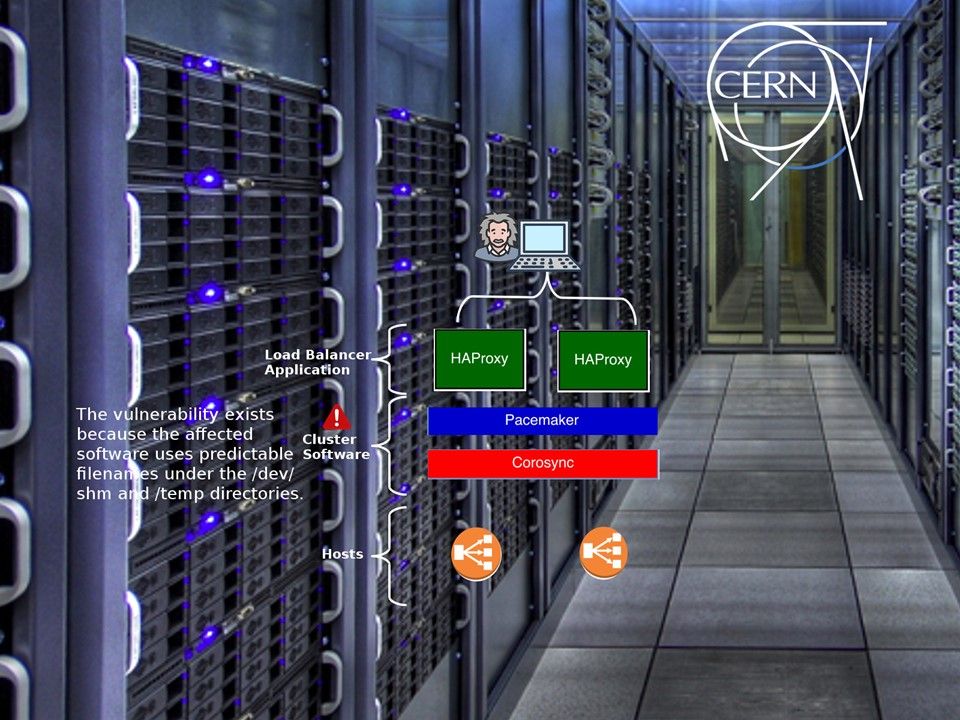
Vulnerability details: A vulnerability in ClusterLabs libqb could allow a local attacker to overwrite arbitrary files on a targeted system. As far as we know, CERN is deployed with this solution. Perhaps this vulnerability not in critical level. However it will let APT group exploit the vulnerability to stolen the data. We don’t need to explain what kind of data stored in CERN. The simple to say, it is the critical data.
Libqb creates files in world-writable directories (/dev/shm, /tmp) with rather predictable file names (e.g. /dev/shm/qb-usbguard-request-7096-835-12-data in case of USBGuard). Also O_EXCL flag is not used when opening the files. This could be exploited by a local attacker to overwrite privileged system files (if not restricted by sandboxing, MAC or symlinking policies).
Reference – If the file already exists beforehand,
Open(pathname, O_RDWR | O_CREAT, 0666); Open successfully, return a fd greater than 0
Open(pathname, O_RDWR | O_CREAT | O_EXCL,0666); Open failed, return -1
O_EXCL indicates that if the file exists when O_CREAT is used, an error message is returned, which can test whether the file exists.
Remedy: ClusterLab releases ver 1.0.5 for bug fix.