Preface: Artificial intelligence especially custom face recognition will be using (ptrace_link). By attaching to another process using the ptrace call, a tool has extensive control over the operation of its target.
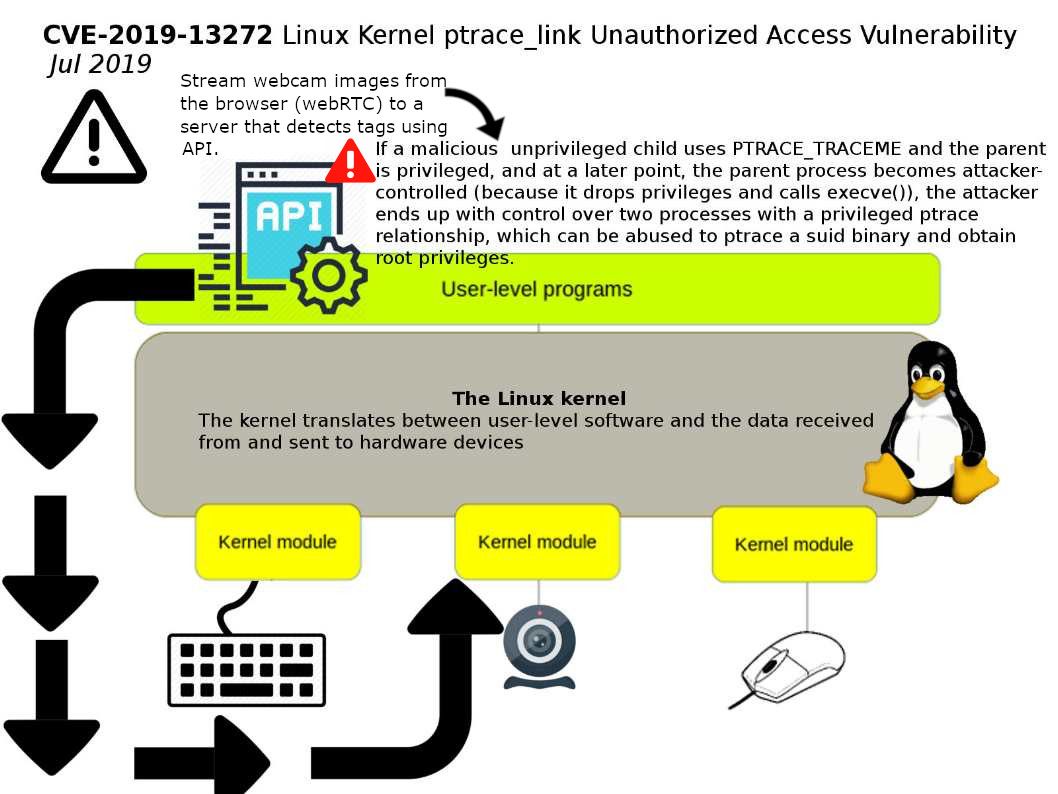
Vulnerability detail: If a malicious unprivileged child uses PTRACE_TRACEME and the parent is privileged, and at a later point, the parent process becomes attacker-controlled (because it drops privileges and calls execve()), the attacker ends up with control over two processes with a privileged ptrace relationship,which can be abused to ptrace a suid binary and obtain root privileges. Above vulnerability could allow a local attacker to perform unauthorized actions on a targeted system.
Remedy: Kernel.org has released a software update. For more information, please refer to the following URL for reference. https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/commit/?id=6994eefb0053799d2e07cd140df6c2ea106c41ee
Remark: Perhaps exploit this vulnerability require local user access. But cyber attacker can use scam email or phishing email to conducting this attack.
I do agree with all the ideas you’ve introduced in your post.
They’re very convincing and can certainly work.
Nonetheless, the posts are too brief for novices. May
just you please extend them a bit from next time? Thank you for
the post.