Preface: A race condition allows an attacker to access a shared resource, which can lead to an attack by other participants using the resource.
Background: VMware Tools is a set of services and modules that enable several features in VMware products for better management of, and seamless user interactions with, guests operating systems.
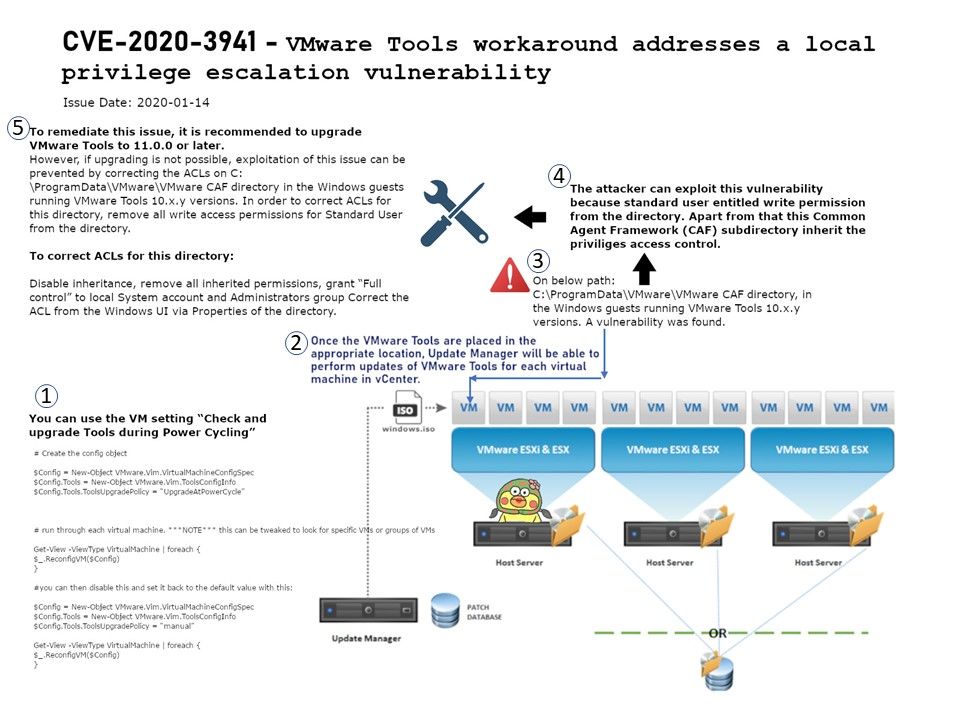
Vulnerability details: The attacker can exploit this vulnerability because standard user entitled write permission from the directory. Apart from that this Common Agent Framework (CAF) subdirectory inherit the priviliges access control.
Remedy: To remediate this issue, it is recommended to upgrade VMware Tools to 11.0.0 or later.
However, if upgrading is not possible, exploitation of this issue can be prevented by correcting the ACLs on “C:\ProgramData\VMware\VMware CAF” directory in the Windows guests running VMware Tools 10.x.y versions. In order to correct ACLs for this directory, remove all write access permissions for Standard User from the directory.
Disable inheritance, remove all inherited permissions, grant “Full control” to local System account and Administrators group Correct the ACL from the Windows UI via Properties of the directory.
Official announcement: Please refer to URL – https://www.vmware.com/security/advisories/VMSA-2020-0002.html