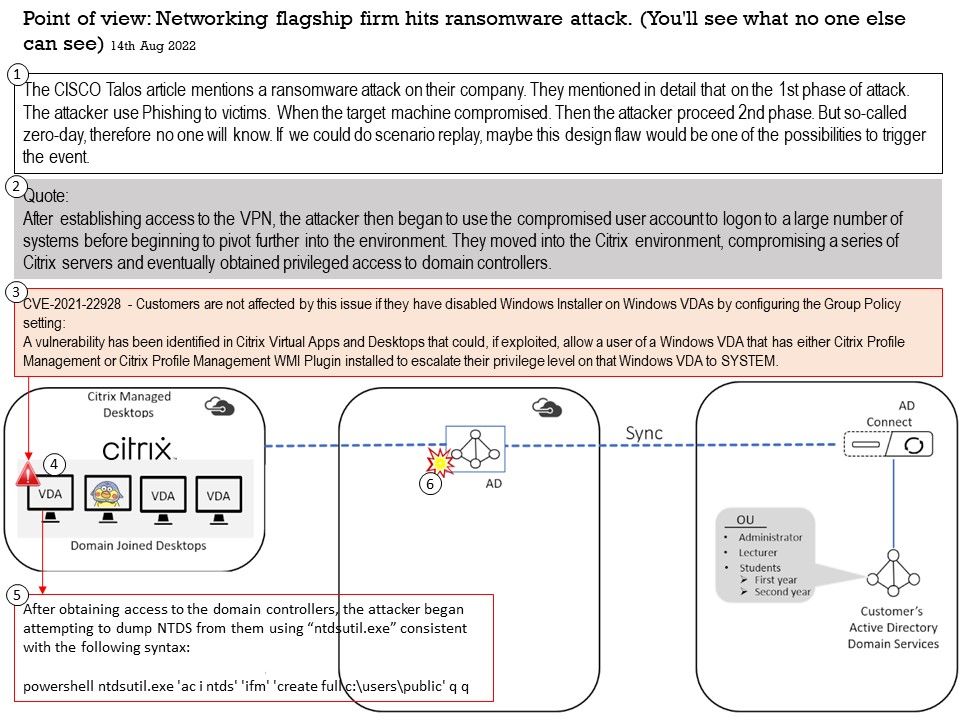
Preface: The CISCO Talos article mentions a ransomware attack on their company. They mentioned in detail that on the 1st phase of attack. The attacker use Phishing to victims. When the target machine compromised. Then the attacker proceed 2nd phase. But so-called zero-day, therefore no one will know. If we could do scenario replay, maybe this design flaw would be one of the possibilities to trigger the event.
Background: In summary and recommendation posted by Talos Intelligence Group (see below):
Cisco implemented a company-wide password reset immediately upon learning of the incident. CTIR previously observed similar TTPs in numerous investigations since 2021.
But so-called zero-day, therefore no one will know. If we could do scenario replay, maybe this design flaw would be one of the possibilities to trigger the event.
CVE-2021-22928 – A vulnerability has been identified in Citrix Virtual Apps and Desktops that could, if exploited, allow a user of a Windows VDA that has either Citrix Profile Management or Citrix Profile Management WMI Plugin installed to escalate their privilege level on that Windows VDA to SYSTEM.
One of the key items I make this speculation: Since we don’t know the exact infrastructure. From a security standpoint, Cisco would not disclose details. But below information provide hints to my interested.
Quote:
After establishing access to the VPN, the attacker then began to use the compromised user account to logon to a large number of systems before beginning to pivot further into the environment. They moved into the Citrix environment, compromising a series of Citrix servers and eventually obtained privileged access to domain controllers.
Official details: If you are interested in digging out the details, please refer to the official website link – https://blog.talosintelligence.com/2022/08/recent-cyber-attack.html
Comment: From a technical point of view, if this is a zero-day vulnerability, I don’t think it can be prevented with preventive or detective controls.