Preface: Even thought CVE-2021-2351 was announced on last year (21st July, 2021), however this topic still lure of my interest. As we know, web server and DB server is an important component in existing digital World. For example, Big data, IoT, automotive and mobility functions will working with front end web server. Whereby in between web server and database server relies on ODBC or JDBC form a bridge do communications to database server. In traditional attack scenario, SQL injection is very common type of attack. When incident happen, it will lost our data confidentiality.
Background: The JDBC thin client is a pure Java, Type IV driver. If you are accessing one type of database, such as Oracle, Sybase and IBM, the preferred driver type is 4.
Oracle Database provides native data network encryption and integrity to ensure that data is secure as it travels across the network. The setup offers two ways to encrypt data over the network, native network encryption and Transport Layer Security (TLS).
In order to cope with confidentiality of data in system design. Encrypting network data provides data privacy so that unauthorized parties cannot view plaintext data as it passes over the network. However, if a design weakness occurs in between devices communication? Do you think what is the exact impact to this defect?
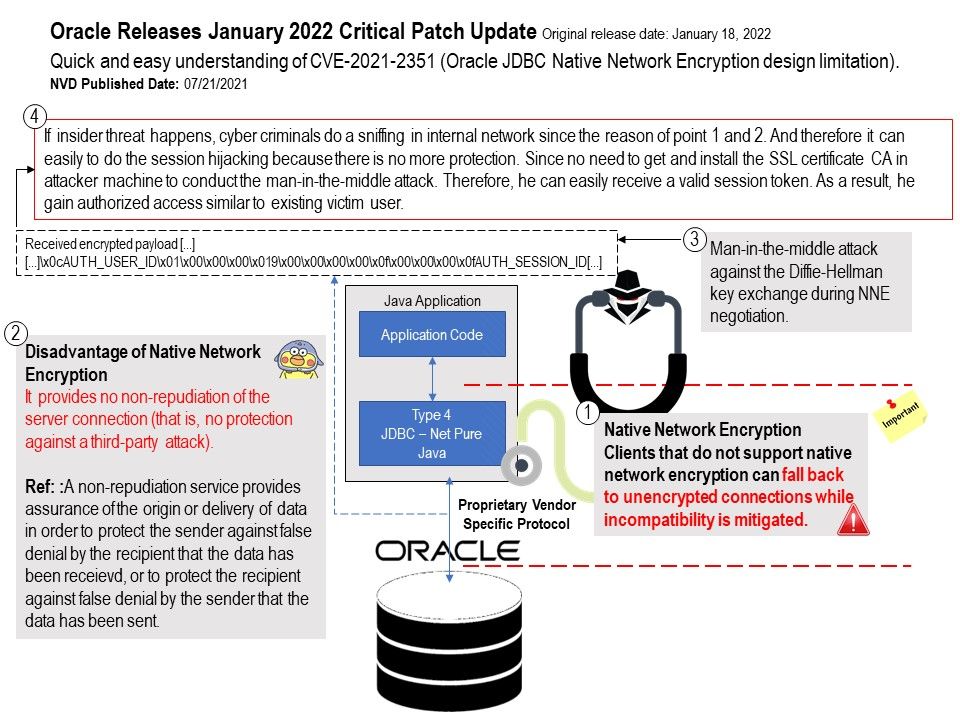
Vulnerability details: There are two fundamental design constraints on this issue (Native Network Encryption).
- Clients that do not support native network encryption can fall back to unencrypted connections while incompatibility is mitigated.
- It provides no non-repudiation of the server connection (that is, no protection against a third-party attack).
When an insider threat occurs, the above 2 design limitations will increase the possibility of being attacked.
Attack scenario: If insider threat happens, cyber criminals do a sniffing in internal network since the reason of point 1 and 2 (refer to attached diagram). And therefore it can easily to do the session hijacking because there is no more protection. Since no need to get and install the SSL certificate CA in attacker machine to conduct the man-in-the-middle attack. Therefore he can easily receive a valid session token. As a result, he gain authorized access similar to existing victim user.
Workaround: Update the Oracle Database servers and clients to the patched versions. Enforce usage of a secured protocol version by setting the following options:
SQLNET.ALLOW_WEAK_CRYPTO_CLIENTS=FALSE (server-side)
SQLNET.ALLOW_WEAK_CRYPTO=FALSE (client-side)
Or use TLS-based transport security instead of Native Network Encryption.
US National Vulnerability Database details announcement – https://nvd.nist.gov/vuln/detail/CVE-2021-2351