Preface: With sandbox technology, Security DevOps team might have easy to conduct test. Since the user can specify exactly what parts of the filesystem should be visible in the sandbox.
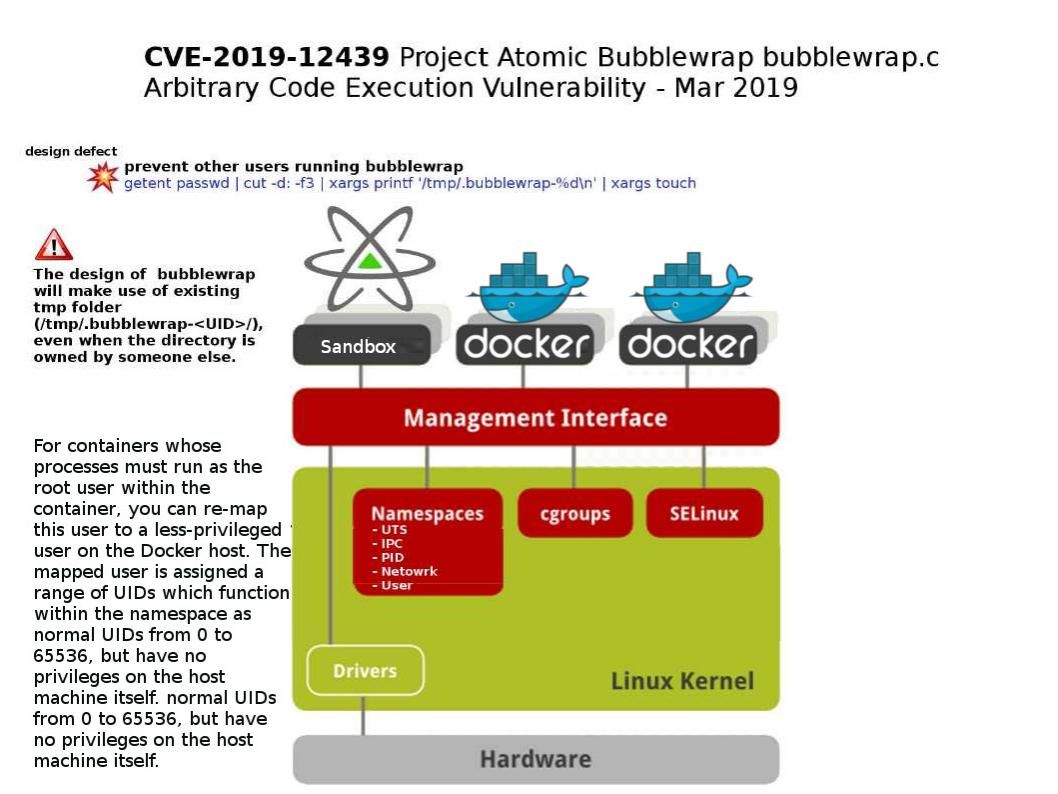
Technical Background: The introduction of user namespaces in the Linux kernel has opened the doors to running containers as default user logins via e.g. ssh or desktop. Bubblewrap, a computing sandbox technology. The goal of bubblewrap is to run an application in a sandbox, where it has restricted access to parts of the operating system or user data such as the home directory. Unlike sandboxes, containers are not a time-limited solution for testing whether code is malicious.
Vulnerability details: A vulnerability in Project Atomic Bubblewrap could allow a local attacker to execute arbitrary code or cause a denial of service (DoS) condition on a targeted system. The vulnerability is due to the insecure use of the /tmp directory by the bubblewrap.c source code file of the affected software.
Remedy: Vendor released software updates at the following link https://github.com/projectatomic/bubblewrap/releases