Preface: Because telnet is not secure, people rely on SSH. Due to design limitations, SSH2 replaces SSH. In fact, SSH2 still has room for improvement.
Technical Background – libssh2 is a client-side C library, which enables applications to connect to an SSH server.
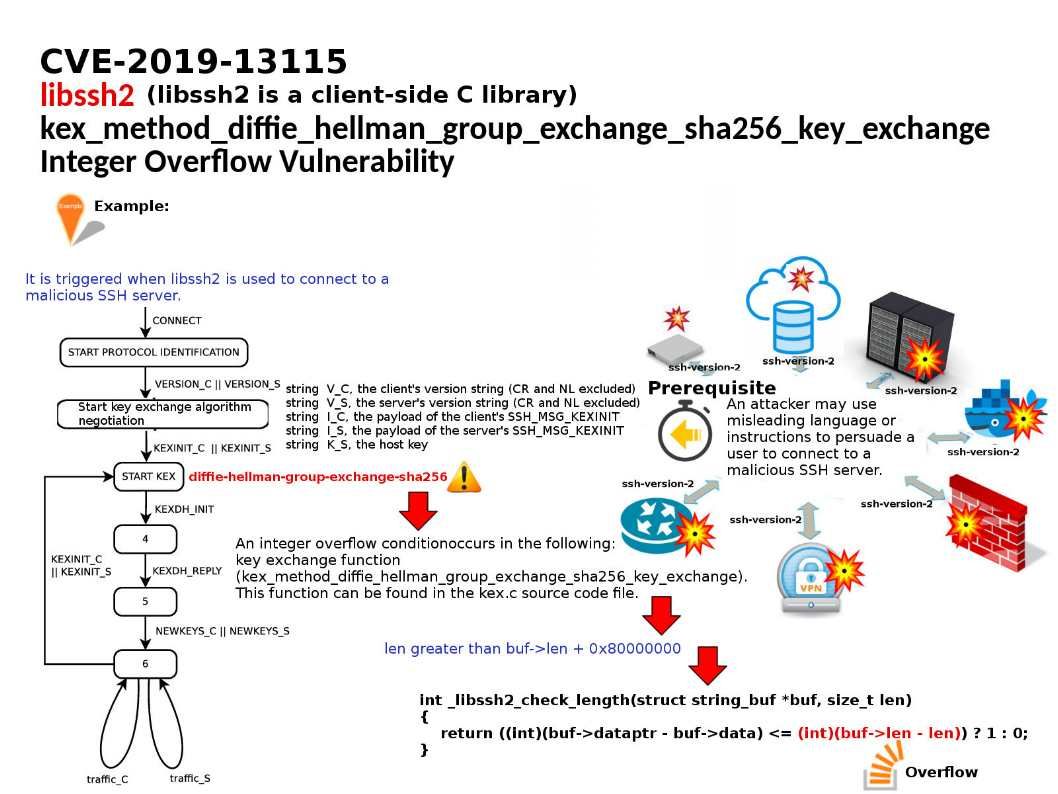
A vulnerability in client-side C library – The vulnerability was triggered when libssh2 is used to connect to a malicious SSH server. The vulnerability is due to an integer overflow condition in the kex_method_diffie_hellman_group_exchange_sha256_key_exchange function, as defined in the kex.c source code file of the affected software.
Remedy – The official statement recommends that users upgrade to version 1.9.0. libssh2 has released software updates at the following link: https://www.libssh2.org/