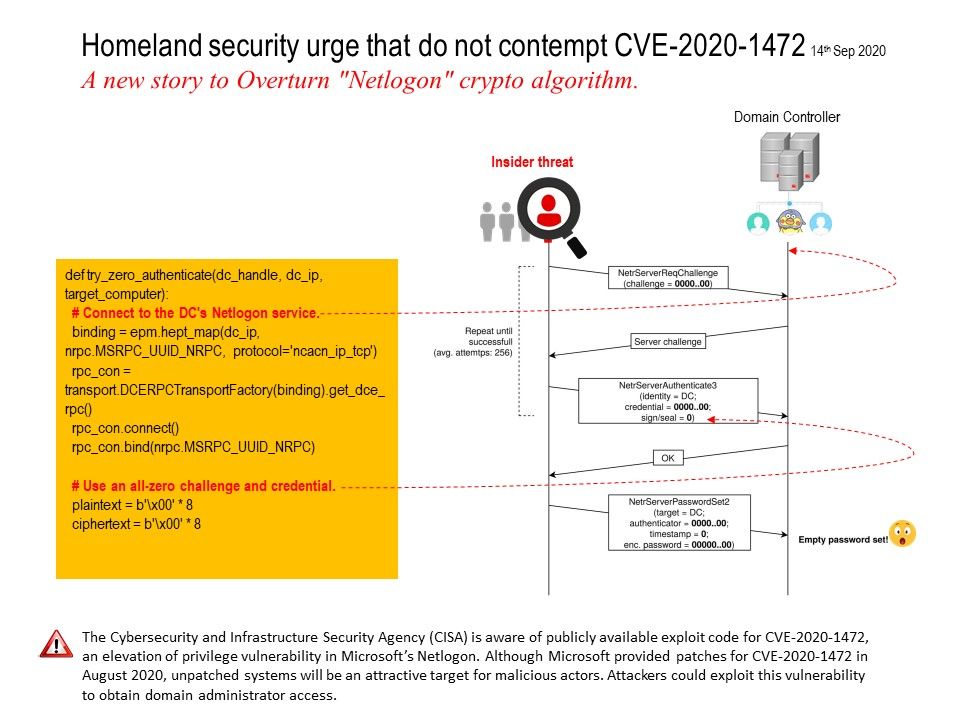
Security Focus:
By sending a number of Netlogon messages in which various fields are filled with zeroes, an attacker can change the computer password of the domain controller that is stored in the AD (refer to Index 1). This can then be used to obtain domain admin credentials and then restore the original DC password.
Index 1: 0 xor 0 = 0 agian, all subsequent blocks fed to AES will be all-zero. And therefore 00 will keep being xorred to the next plaintext bytes.
Important notice by US Homeland Security:
The Cybersecurity and Infrastructure Security Agency (CISA) is aware of publicly available exploit code for CVE-2020-1472, an elevation of privilege vulnerability in Microsoft’s Netlogon. Although Microsoft provided patches for CVE-2020-1472 in August 2020, unpatched systems will be an attractive target for malicious actors. Attackers could exploit this vulnerability to obtain domain administrator access.
Reference: https://us-cert.cisa.gov/ncas/current-activity/2020/09/14/exploit-netlogon-remote-protocol-vulnerability-cve-2020-1472