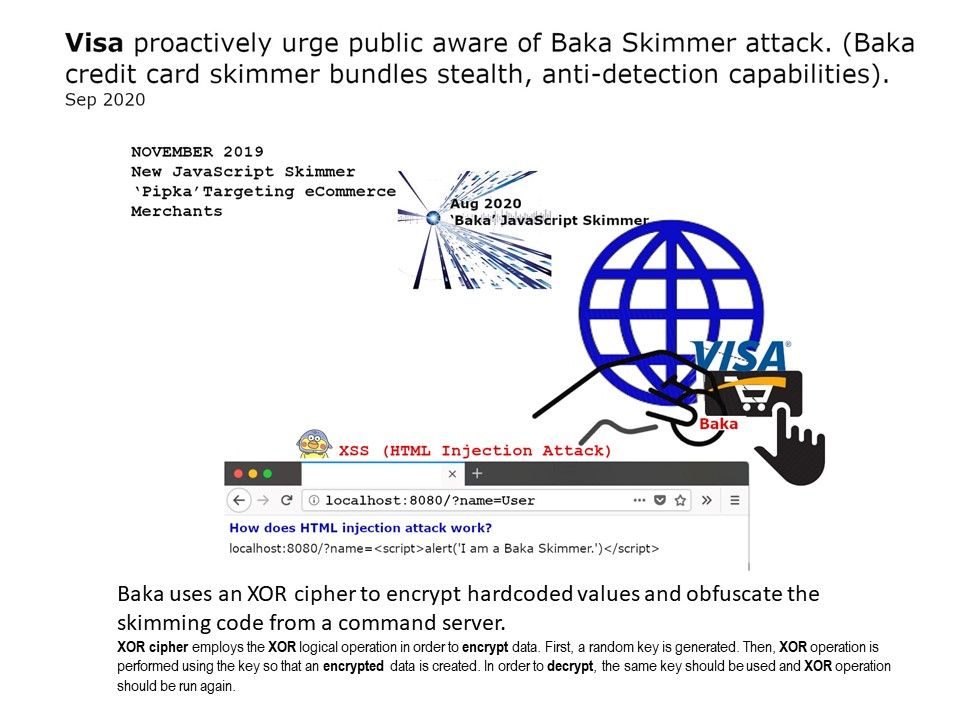
Preface: Visa identified a previously unknown eCommerce skimmer, and named the skimmer ‘Baka’.
Synopsis: The malicious JavaScript code aimed to avoid detection for modern defense system. Baka is stealth, anti-detection capabilities.
According to an alert from Visa’s Payment Fraud Disruption (PFD) division, the skimmer also attempts to avoid detection and analysis by “removing itself from memory when it detects the possibility of dynamic analysis with Developer Tools or when data has been successfully exfiltrated”.
Reference: Visa security alert – https://usa.visa.com/content/dam/VCOM/global/support-legal/documents/visa-security-alert-baka-javascript-skimmer.pdf
Additional: Briefly describe the concept of attack. The attacker sneaks some malicious JavaScript (usually via a <script> tag) into your html which is then executed.
How to protect against this attack?
– Sanitizing at the url param layer
– Sanitizing at the templating layer