Published: 2025-08-20
Updated: 2025-08-19
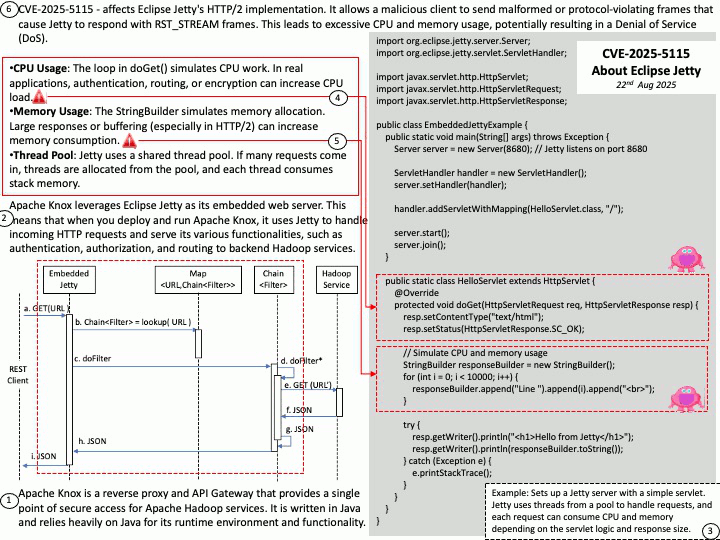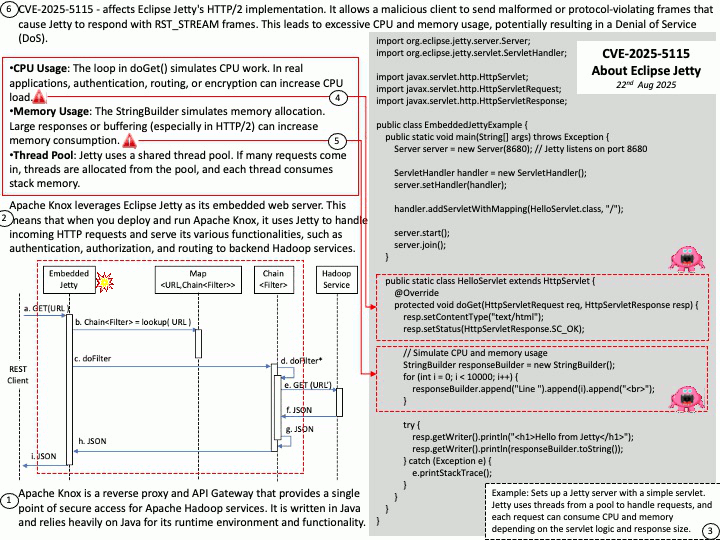
Preface: Apache Knox uses Eclipse Jetty as its embedded web server. When you deploy and execute Apache Knox, it uses Jetty to handle incoming HTTP requests and provide its various features, such as authentication, authorization, and routing to backend Hadoop services.
Ref: Is Hadoop used in AI? Hadoop ecosystems help with the processing of data and model training operations for machine learning applications.
Background: How Jetty Consumes Resources? Apache Knox leverages Eclipse Jetty as its embedded web server. Apache Knox is a reverse proxy and API Gateway that provides a single point of secure access for Apache Hadoop services. It is written in Java and relies heavily on Java for its runtime environment and functionality.
Is the Exploit Related to HTTP Response Buffer Size?
Not directly. The vulnerability does not exploit the size of the HTTP response buffer itself. Instead, it targets the processing logic of incoming HTTP/2 frames. However:
- If Jetty is configured with large buffers or many concurrent streams, the impact of the exploit can be amplified.
- The server may allocate response buffers unnecessarily if it begins processing a request before realizing it’s invalid.
Vulnerability details: In Eclipse Jetty, versions <=9.4.57, <=10.0.25, <=11.0.25, <=12.0.21, <=12.1.0.alpha2, an HTTP/2 client may trigger the server to send RST_STREAM frames, for example by sending frames that are malformed or that should not be sent in a particular stream state, therefore forcing the server to consume resources such as CPU and memory.
Official announcement: Please see the link for details –