Published: 2025-08-22
Updated: 2025-08-21
Preface: In Chrome, a sandbox is a security feature that isolates web content and processes into restricted environments, while serialization is the process of converting an object’s state into a format (like a byte stream) that can be stored or transferred. The sandbox focuses on security and isolation, whereas serialization is a data handling mechanism used within various Chrome features, such as interacting with hardware via the Serial AP.
Background: In Chrome, an unprivileged environment is a restricted sandbox where web content and extensions run with limited access to the operating system and local resources, designed to prevent malicious code from causing harm. Chrome uses sandboxing, process isolation, and a permissions system to enforce this isolation. Content running in an unprivileged environment generally cannot install programs, view or delete user data, or directly interact with system-level features unless the user explicitly grants specific permissions.
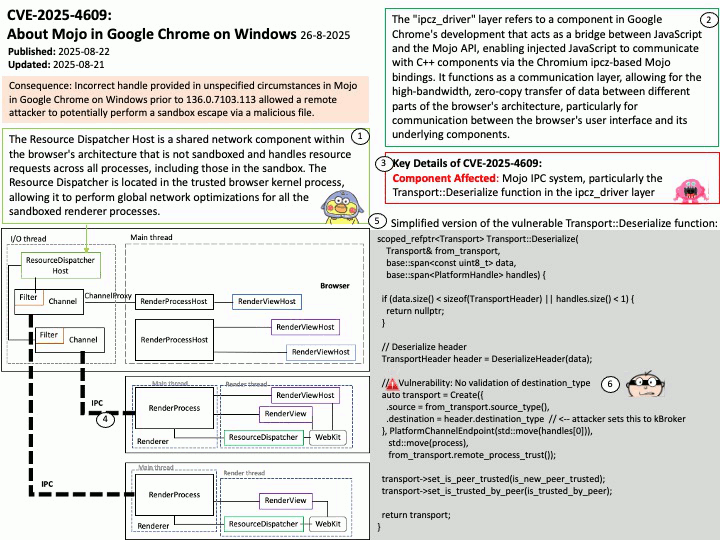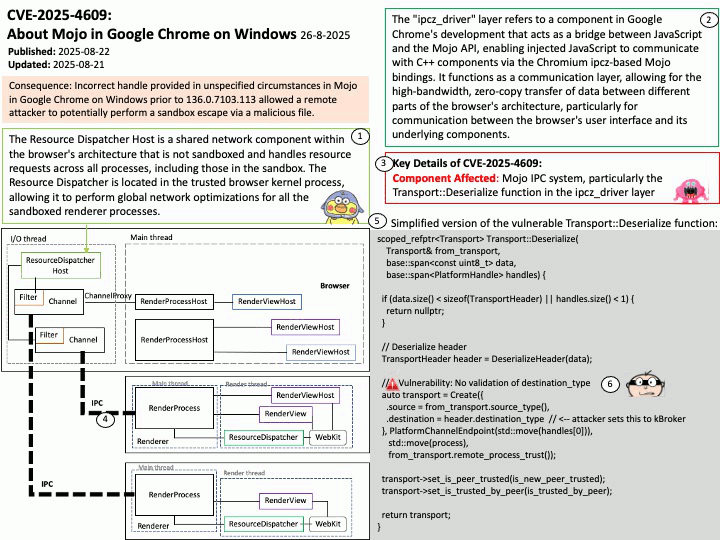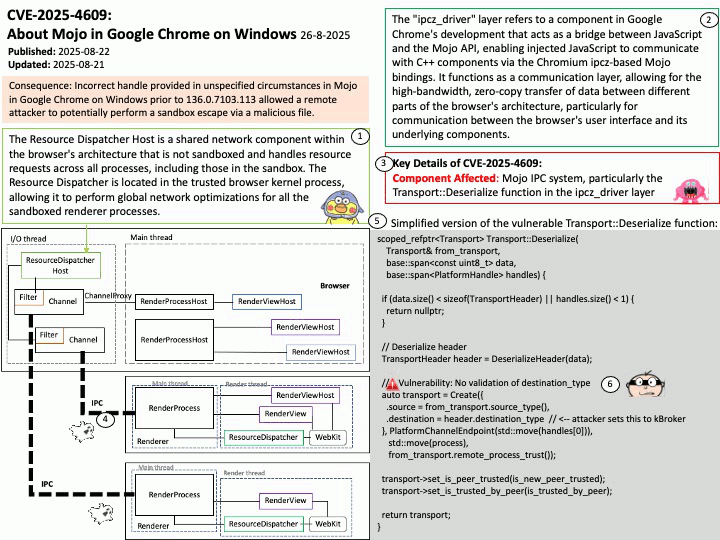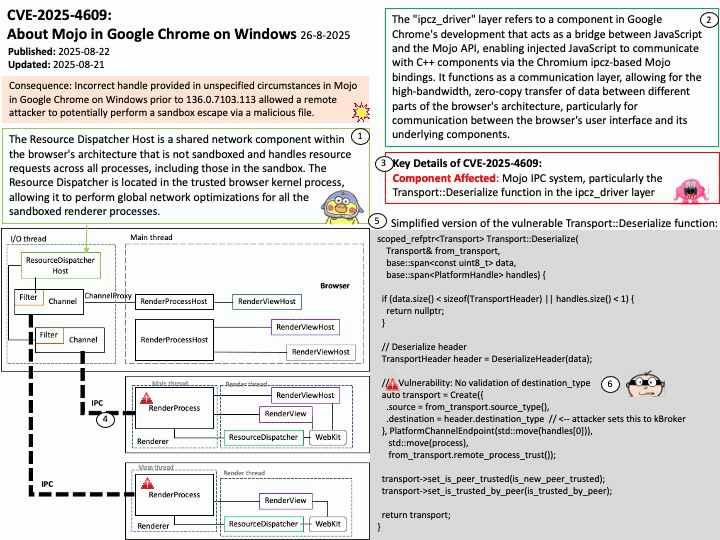
Ref: The “ipcz_driver” layer refers to a component in Google Chrome’s development that acts as a bridge between JavaScript and the Mojo API, enabling injected JavaScript to communicate with C++ components via the Chromium ipcz-based Mojo bindings. It functions as a communication layer, allowing for the high-bandwidth, zero-copy transfer of data between different parts of the browser’s architecture, particularly for communication between the browser’s user interface and its underlying components.
Vulnerability details: Incorrect handle provided in unspecified circumstances in Mojo in Google Chrome on Windows prior to 136.0.7103.113 allowed a remote attacker to potentially perform a sandbox escape via a malicious file.
Official announcement: Please see the link for details –