Preface: A NUMA system is a computer platform that comprises multiple components or assemblies each of which may contain 0 or more CPUs, local memory, and/or IO buses.
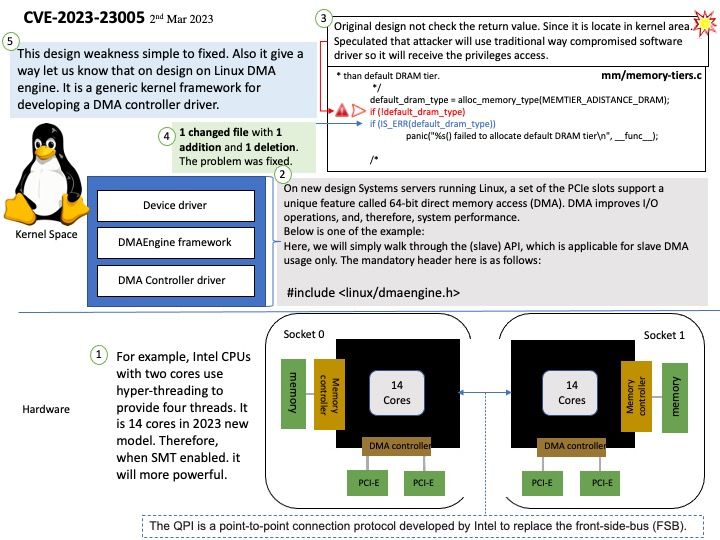
Background: On new design Systems servers running Linux, a set of the PCIe slots support a unique feature called 64-bit direct memory access (DMA). DMA improves I/O operations, and, therefore, system performance.
The DMA engine is a generic kernel framework for developing a DMA controller driver. The main goal of DMA is offloading the CPU when it comes to copy memory. A pointer variable whose value is under kernel control and guaranteed by the kernel to always point into the kernel’s memory space, and hence is trustworthy. User pointers should always be verified to refer to user-level memory before being dereferenced.
Vulnerability details: In the Linux kernel before 6.2, mm/memory-tiers.c misinterprets the alloc_memory_type return value (expects it to be NULL in the error case, whereas it is actually an error pointer).
alloc_memory_type() returns error pointers on error instead of NULL. Use IS_ERR() to check the return value to fix this.
Official details: For details, see the link for reference – https://nvd.nist.gov/vuln/detail/CVE-2023-23005