Preface: Top Programming Languages for Android App Development in 2023 · Most Popular Programming Languages for Android · Kotlin · Java · C# · C++/C · Python. What is C language use-after-free. Use-After-Free (UAF) is a vulnerability related to incorrect use of dynamic memory during program operation. If after freeing a memory location, a program does not clear the pointer to that memory, an attacker can use the error to hack the program.
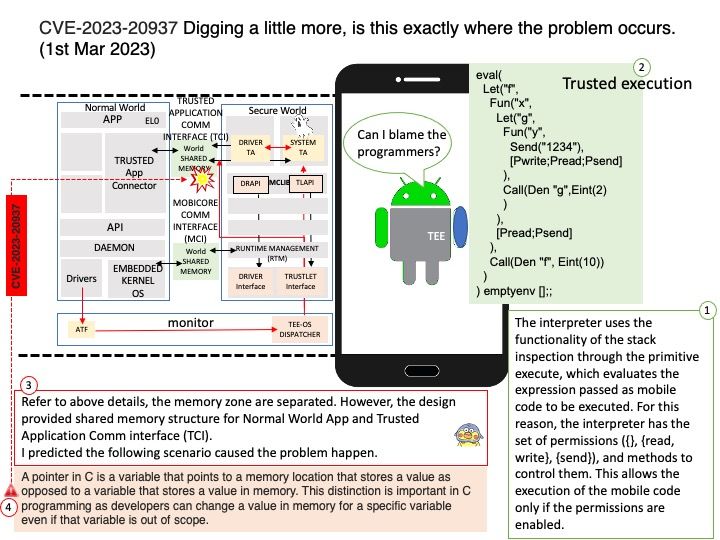
Background: The Trusty OS runs on the same processor as the Android OS, but Trusty is isolated from the rest of the system by both hardware and software.Trusty provides APIs for developing two classes of applications/services: Trusted applications or services that run on the TEE processor.
Android uses the concept of user-authentication-gated cryptographic keys that requires cryptographic key storage and service provider and user authenticators. Android 9 and higher includes Protected Confirmation, which gives users a way to formally confirm critical transactions, such as payments.
Vulnerability details: In several functions of the Android Linux kernel, there is a possible way to corrupt memory due to a use after free. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.
Observation: A pointer in C is a variable that points to a memory location that stores a value as opposed to a variable that stores a value in memory. This distinction is important in C programming as developers can change a value in memory for a specific variable even if that variable is out of scope.
I predicted above matter caused the problem happen in shared memory environment.
Official details: See url links for details – https://nvd.nist.gov/vuln/detail/CVE-2023-20937