Preface: What is Samsung TEEGRIS? Samsung TEEGRIS is a system-wide security solution that allows you to run applications in a trusted execution environment based on TrustZone. We present the TEEGRIS architecture for external developers to enable their trusted applications and services.
Background: TEEGRIS is a relatively recent TEE OS, introduced by Samsung on the Galaxy S10. Most of the newer (starting from 2019) Samsung phones that have Exynos chipsets will also have TEEGRIS running in the TEE.
AArch64 or ARM64 is the 64-bit extension of the ARM architecture family. It was first introduced with the Armv8-A architecture. ARMv8-A CPUs support four privilege levels for each “world”, also known as exception levels:
- (S-)EL0 – user mode/app
- (S-)EL1 – kernel
- EL2 – hypervisor
- EL3 – Secure Monitor – EL3 is the level above which is called Monitor Mode. This extra level is used to run security applications (Trustzone).
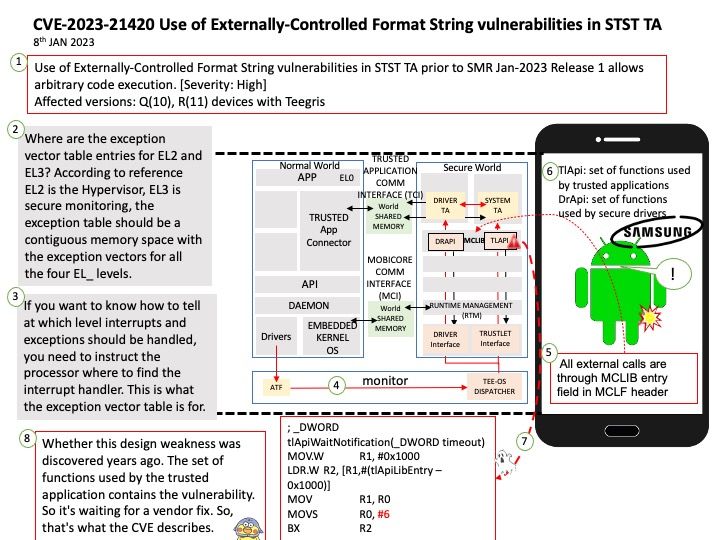
Where are the exception vector table entries for EL2 and EL3? According to reference EL2 is the Hypervisor, EL3 is secure monitoring, the exception table should be a contiguous memory space with the exception vectors for all the four EL_ levels.
Remark: If you want to know how to tell at which level interrupts and exceptions should be handled, you need to instruct the processor where to find the interrupt handler. This is what the exception vector table is for.
- TlApi: set of functions used by trusted applications
- DrApi: set of functions used by secure drivers
Whether this design weakness was discovered years ago. The set of functions used by the trusted application contains the vulnerability. So it’s waiting for a vendor fix. So, that’s what the CVE describes.
Vulnerability details:
Severity: High
Affected versions: Q(10), R(11) devices with Teegris
Reported on: June 3, 2022
Disclosure status: Privately disclosed
Use of Externally-Controlled Format String vulnerabilities in ([ST] Samsung TEEgris Security Target, STST TA prior to SMR Jan-2023 Release 1 allows arbitrary code execution.
The patch restricts the triggering for the print of externally controlled format string code.
Official announcement: SMR-JAN-2023 – Samsung Mobile is releasing a maintenance release for major flagship models as part of monthly Security Maintenance Release (SMR) process. This SMR package includes patches from Google and Samsung.
For more information on this design weakness, see the link – https://security.samsungmobile.com/securityUpdate.smsb