Preface: Every Fortinet product has a built-in administrator account.
Background: Ten years ago, one of the key function is reset function in business contingency program. Refer to textbooks, the objective of disaster recovery is resume the service. So more terms created: Recovery Point Objective (RPO) Recovery Time Objective (RTO) Work Recovery Time (WRT) Maximum Tolerable Downtime (MTD).
How about critical service device especially firewall appliance? There is no difference. At that time, cyber security standard is not enforce into today standard.
The password reset procedure, it all depends on manufacturer hardware design.
So if the recovery procedure only can do in privilege account. So it compliance to minimum standard. The information security so called access privilege control.
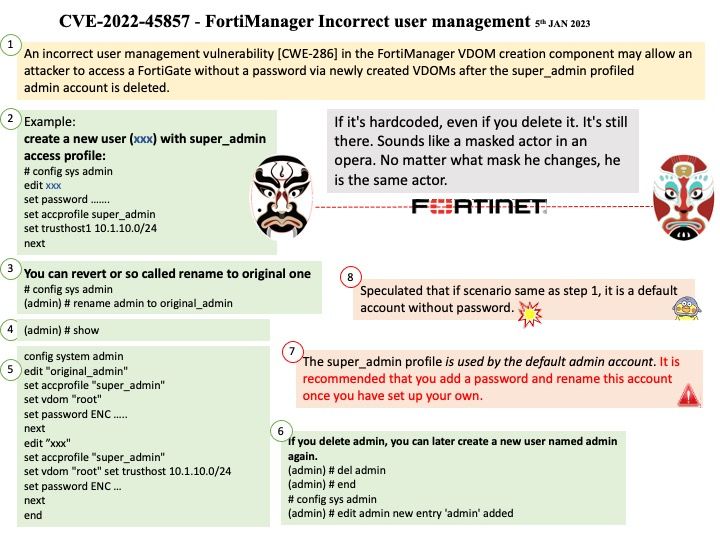
Vulnerability details: An incorrect user management vulnerability [CWE-286] in the FortiManager VDOM creation component may allow an attacker to access a FortiGate without a password via newly created VDOMs after the super_admin profiled admin account is deleted.
Affected Products
At least
FortiManager version 7.0.0 through 7.0.1
FortiManager version 6.4.0 through 6.4.7
FortiManager version 6.2.0 through 6.2.8
Solutions
Please upgrade to FortiManager version 7.0.2 or above
Please upgrade to FortiManager version 6.4.8 or above
Please upgrade to FortiManager version 6.2.9 or above
Official announcement: Please refer to link – https://www.fortiguard.com/psirt/FG-IR-22-371