Preface: Companies like SlideShare, Airbnb, CrunchBase, Bloomberg, Dribble, Shopify, and GitHub have trusted Ruby on Rails and used the framework in their applications.
Background: Ruby is an open source, object oriented language that was developed in the mid-90s. Since it is a scripting language. Ruby doesn’t talk to the hardware directly. Rather, it is written in a text file and parsed by an interpreter before it can be turned into code.
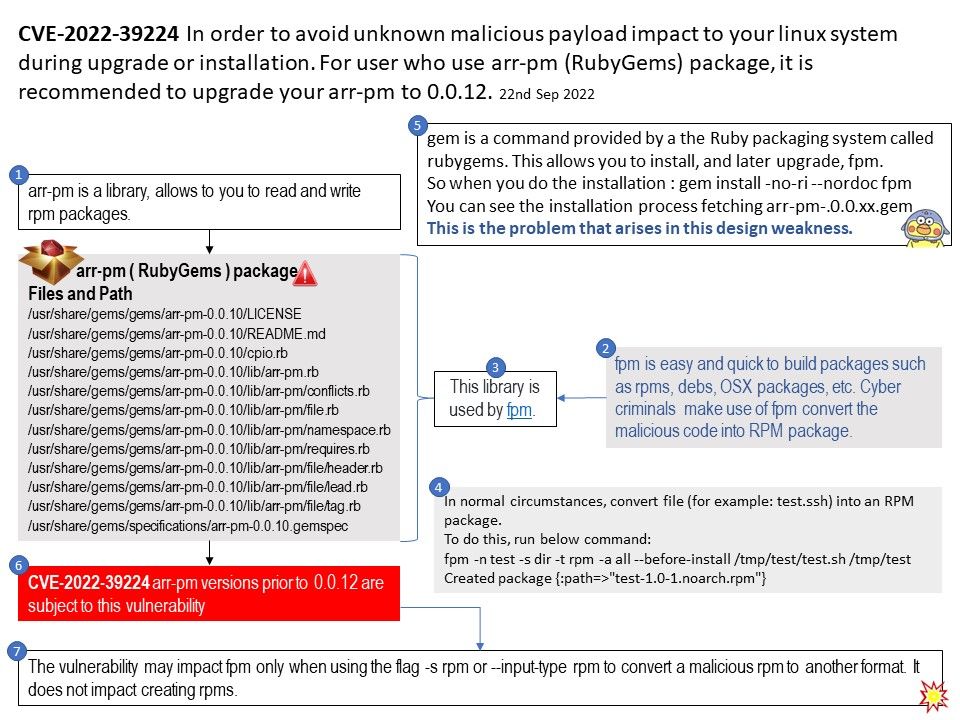
The library (arr-pm) allows to you to read and write rpm packages. It is written in pure ruby because librpm is not available on all systems.
This programming language is also used in automation, website deployment, and DevOps.
Vulnerability details: Vulnerability details: Arr-pm is an RPM reader/writer library written in Ruby. Versions prior to 0.0.12 are subject to OS command injection resulting in shell execution if the RPM contains a malicious “payload compressor” field. This vulnerability impacts the extract and files methods of the RPM::File class of this library.
Additional: The vulnerability may impact fpm only when using the flag -s rpm or –input-type rpm to convert a malicious rpm to another format. It does not impact creating rpms.
gem is a command provided by a the Ruby packaging system called rubygems. This allows you to install, and later upgrade, fpm.
So when you do the installation : gem install -no-ri –nordoc fpm
You can see the installation process fetching arr-pm-.0.0.xx[.]gem
This is the problem that arises in this design weakness.
Solution: It is recommended to upgrade your arr-pm to 0.0.12.
09/02/2022 CVE reserved
09/22/2022 +20 days Advisory disclosed