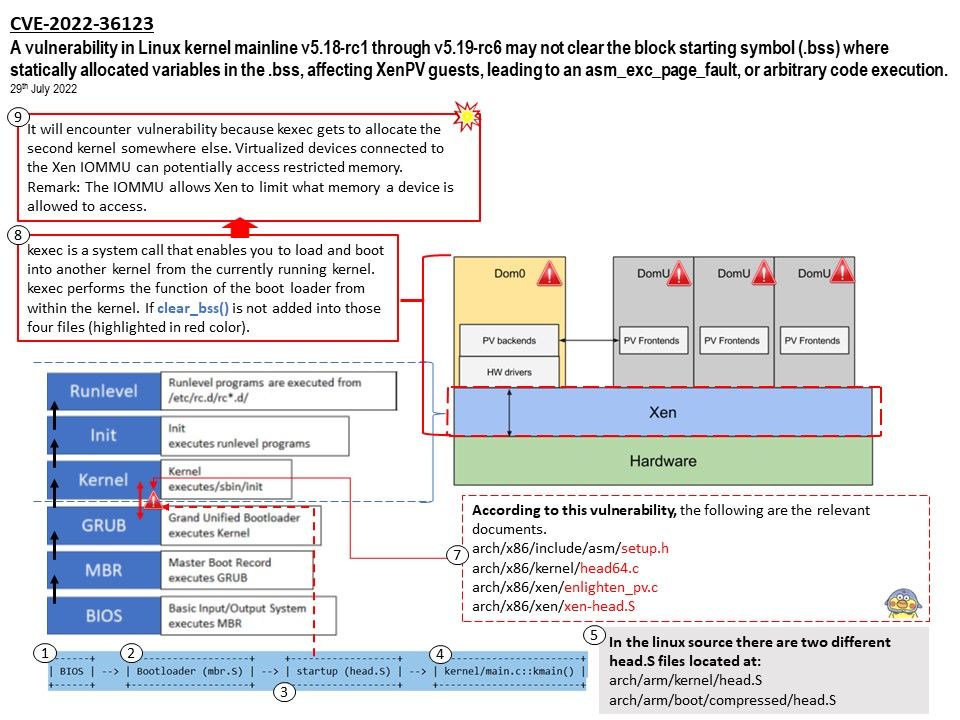
Preface: Uninitialized data segment, often called the “bss” segment, named after an ancient assembler operator that stood for “block started by symbol.” Data in this segment is initialized by the kernel to arithmetic 0 before the program starts executing.
Background: Xen is an open-source baremetal hypervisor that is widely used by commercial and non-commercial platforms to provide virtualization support.
Dom0 is the initial domain started by the Xen hypervisor on boot. Dom0 is an abbrevation of “Domain 0” (sometimes written as “domain zero” or the “host domain”). Dom0 is a privileged domain that starts first and manages the DomU unprivileged domains. The Xen hypervisor is not usable without Dom0.
Vulnerability details: The Linux kernel before 5.18.13 lacks a certain clear operation for the block starting symbol (.bss). This allows Xen PV guest OS users to cause a denial of service or gain privileges. For details, please refer to attached diagram.
Instead of clearing the bss area in assembly code, use the clear_bss()function.This requires to pass the start_info address as parameter to xen_start_kernel() in order to avoid the xen_start_info being zeroed again.
Details released by NIST: Please refer to the link – https://cve.report/CVE-2022-36123