Preface: Mali GPU kernel drivers have a wide range of applications in the IoT and IIoT world. Even the auto industry, gaming, healthcare and artificial intelligence.
Background:The Android and Linux version of the Mali GPUs Device Driver provide low-level access to the Mali GPUs that are part of the Valhall family. Some of these components are being made available under the GPLv2 licence. The company named “ARM”. They provides access to the source packages from which loadable kernel modules can be built.
The Mali GPU kernel device driver handles the following. Access to the Mali GPU hardware, Interrupt handling and Low level memory management.
Example:
Question: In normal circumstances, when program (software driver or software application) called kmalloc and didn’t free that memory before rmmod was called on the module, what happens to that memory? Is it a memory leak and it is completely unusable until restart, or does the kernel free that memory automatically?
Answer: It won’t be freed until explicitly done. Memory allocated with kmalloc() needs to be freed using kfree(). That piece of memory stays till the system is on.
Vulnerability details: An issue was discovered in the Arm Mali GPU Kernel Driver (Valhall r29p0 through r38p0). A non-privileged user can make improper GPU processing operations to gain access to already freed memory.
The software performs operations on a memory buffer, but it can read from or write to a memory location that is outside of the intended boundary of the buffer.
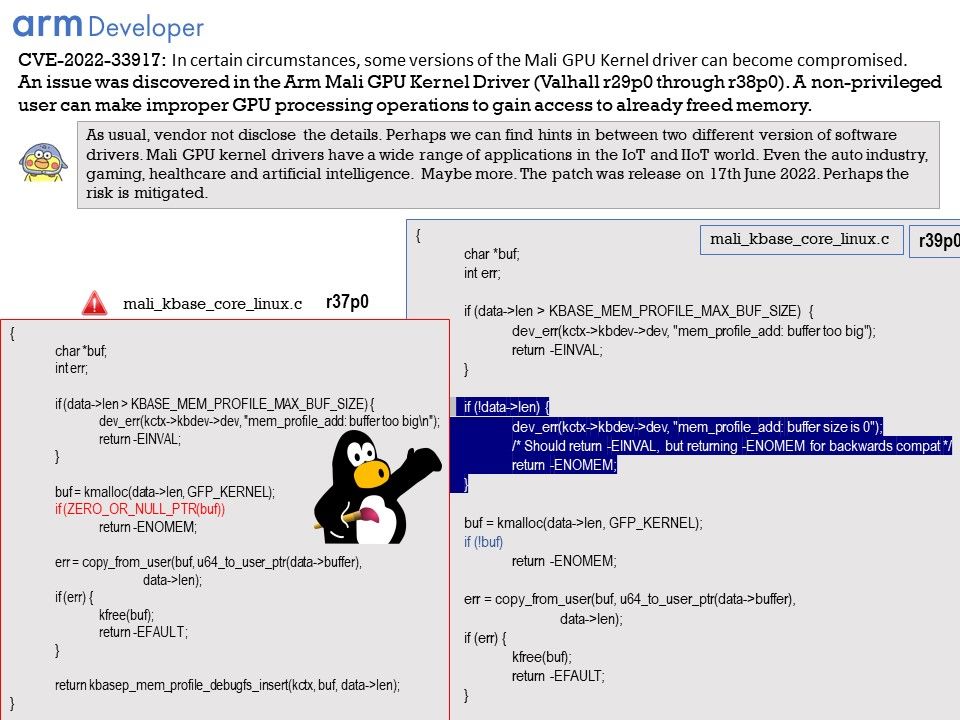
As usual, vendor not disclose the details. Perhaps we can find hints in between two different version of software drivers.
Please refer to attached image for details.
Solution: This issue is fixed in Valhall GPU Kernel Driver r39p0. Users are recommended to upgrade if they are impacted by this issue. Please refer to the link for details – https://developer.arm.com/Arm%20Security%20Center/Mali%20GPU%20Driver%20Vulnerabilities
Remark: The patch was release on 17th June 2022. Perhaps the risk is mitigated.