Preface: Security misconfiguration vulnerabilities take place when an application component is vulnerable to attack as a result of insecure configuration option or misconfiguration.
Background: AWS Systems Manager (formerly known as SSM) is Amazon software that runs on Amazon Elastic Compute Cloud (Amazon EC2) instances, edge devices, and on-premises servers and virtual machines (VMs). A managed node is any machine configured for Systems Manager. Systems Manager supports Amazon Elastic Compute Cloud (Amazon EC2) instances, edge devices, and on-premises servers and virtual machines (VMs), including VMs in other cloud environments. SSM Agent makes it possible for Systems Manager to update, manage, and configure these resources.
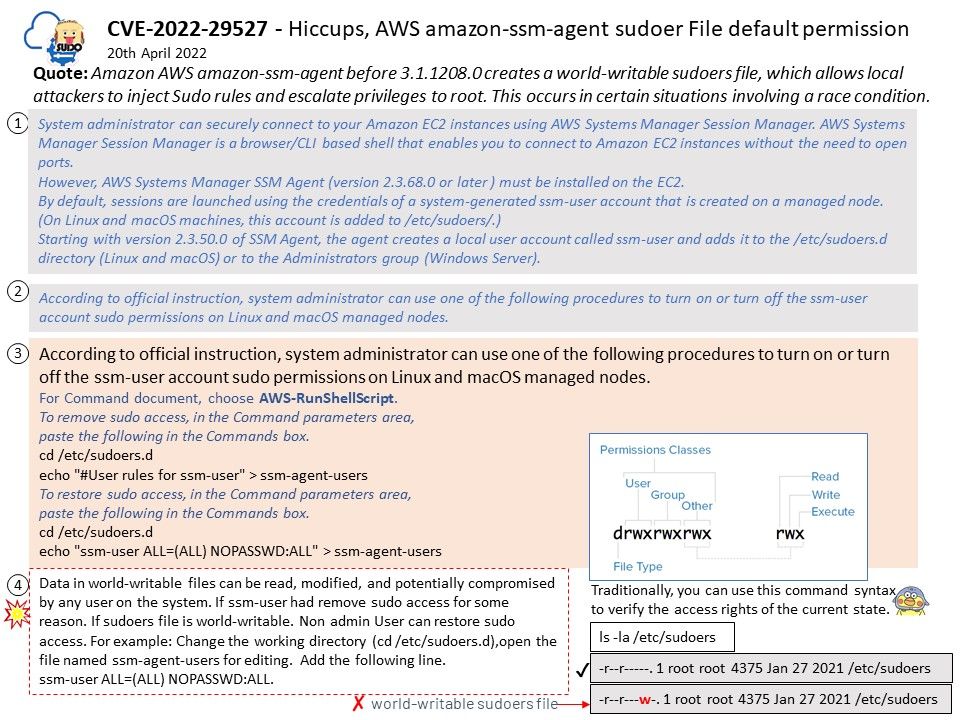
System administrator can securely connect to your Amazon EC2 instances using AWS Systems Manager Session Manager. AWS Systems Manager Session Manager is a browser/CLI based shell that enables you to connect to Amazon EC2 instances without the need to open ports.
However, AWS Systems Manager SSM Agent (version 2.3.68.0 or later ) must be installed on the EC2.
By default, sessions are launched using the credentials of a system-generated ssm-user account that is created on a managed node. (On Linux and macOS machines, this account is added to /etc/sudoers/.)
Starting with version 2.3.50.0 of SSM Agent, the agent creates a local user account called ssm-user and adds it to the /etc/sudoers.d directory (Linux and macOS) or to the Administrators group (Windows Server).
Vulnerability details: Amazon AWS amazon-ssm-agent before 3.1.1208.0 creates a world-writable sudoers file, which allows local attackers to inject Sudo rules and escalate privileges to root. This occurs in certain situations involving a race condition.
Ref: In layman terms, a race condition can be defined as, a condition in which two or more threads compete together to get certain shared resources. For example, if thread A is reading data from the linked list and another thread B is trying to delete the same data.
Data in world-writable files can be read, modified, and potentially compromised by any user on the system. If ssm-user had remove sudo access for some reason. If sudoers file is world-writable. Non admin User can restore sudo access. For example: Change the working directory (cd /etc/sudoers.d),open the file named ssm-agent-users for editing. Add the following line.
ssm-user ALL=(ALL) NOPASSWD:ALL.
Remedy: Amazon SSM Agent – Release 3.1.1260.0 – 2022-04-12. Please refer to the link for details – https://github.com/aws/amazon-ssm-agent/releases/tag/3.1.1260.0