Preface: In medium to small size firm, software developer is busy to achieve their company objective. Perhaps cyber security is not the priority of their awareness. The software version control is major successful factor of their software development. Perhaps they will make use of Git LFS (Large File Storage).
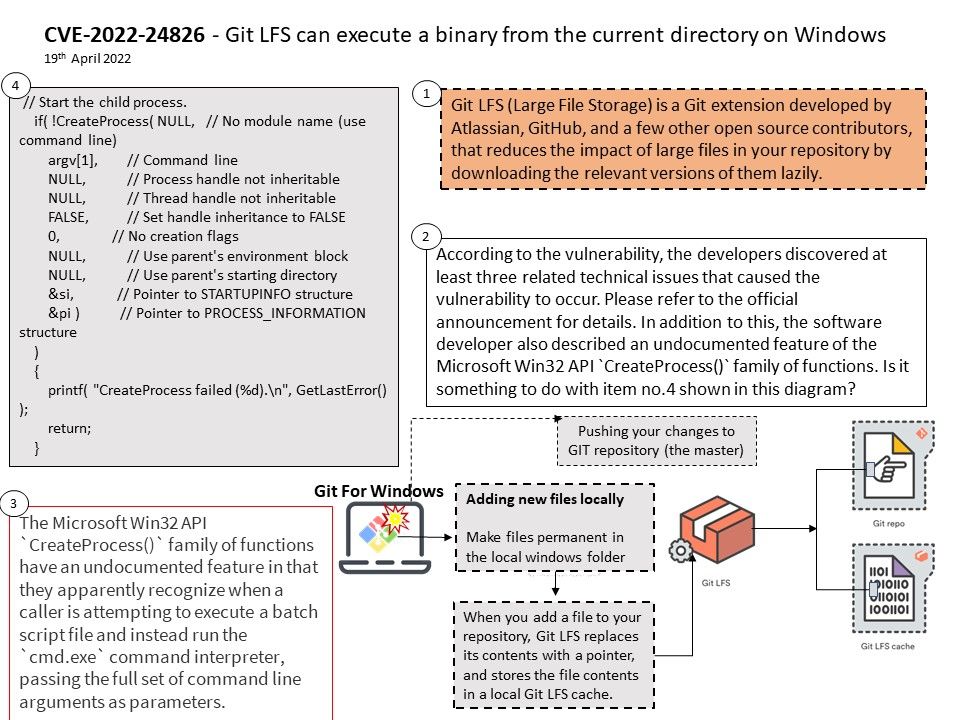
Background: What is a git LFS? Git LFS (Large File Storage) is a Git extension developed by Atlassian, GitHub, and a few other open source contributors, that reduces the impact of large files in your repository by downloading the relevant versions of them lazily. The git repository is github. It is free unless you want to create a private repository. For private repositories you have to pay a monthly price but it is not mandatory. GitHub’s recommended maximum file size of 50 MB. If your push operation failed because file size exceeded limit. The solution to this is to install Git Large File Storage support.
Managing large files such as audio, video and graphics files has always been one of the shortcomings of Git. The general recommendation is to not have Git repositories larger than 1 GB to preserve performance.
Vulnerability details: On Windows, if Git LFS operates on a malicious repository with a ..exe file as well as a file named git[.]exe, and git[.]exe is not found in PATH, the ..exe program will be executed, permitting the attacker to execute arbitrary code.
Similarly, if the malicious repository contains files named ..exe and cygpath[.]exe, and cygpath[.]exe is not found in PATH, the ..exe program will be executed when certain Git LFS commands are run.
Remark: This does not affect Unix systems.
Remedy: Git LFS has resolved this vulnerability by always reporting an error when a program is not found in any directory listed in PATH rather than passing an empty string to the Go os/exec package in this case.
The bug in the Go os/exec package has been reported to the Go project and is expected to be patched after this security advisory is published.
The problem was introduced in v2.12.1 and is patched in v3.1.3 and v3.1.4. Users of affected versions should upgrade to v3.1.4.