Preface: kdump is a feature of the Linux kernel that creates crash dumps in the event of a kernel crash. When triggered, kdump exports a memory image (also known as vmcore) that can be analyzed for the purposes of debugging and determining the cause of a crash.
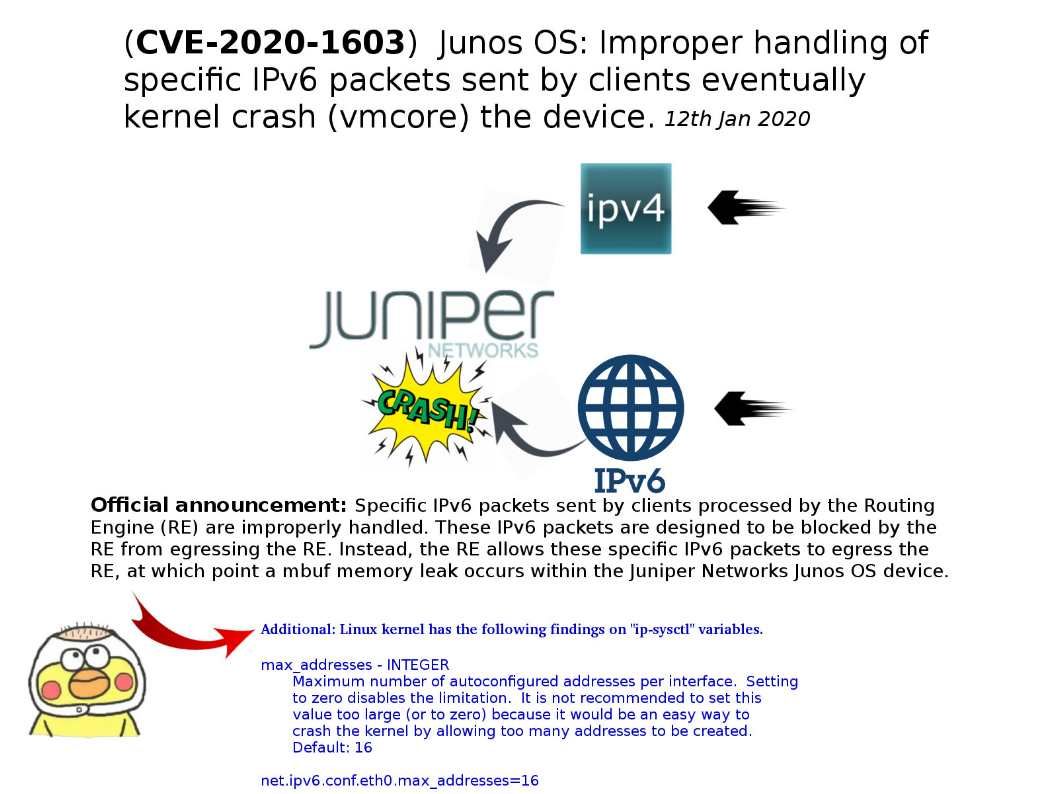
Vulnerability details: Improper handling of specific IPv6 packets sent by clients mbuf and let memory leak occurs. This memory leak eventually leads to a kernel crash (vmcore), or the device hanging and requiring a power cycle to restore service, creating a Denial of Service (DoS) condition.
Official announcement and remedy solution:https://kb.juniper.net/InfoCenter/index?page=content&id=JSA10982&cat=SIRT_1&actp=LIST
Additional possibilities – handling IPv6 packet design weakness
a. The server side sets IPV6_RECVPKTINFO on a listening socket, and the client side just sends a message to the server. Then the kernel panic occurs on the server.
b. net.ipv6.conf.eth0.max_addresses=16 It is not recommended to set this value too large (or to zero) because it would be an easy way to crash the kernel by allowing too many addresses to be created.