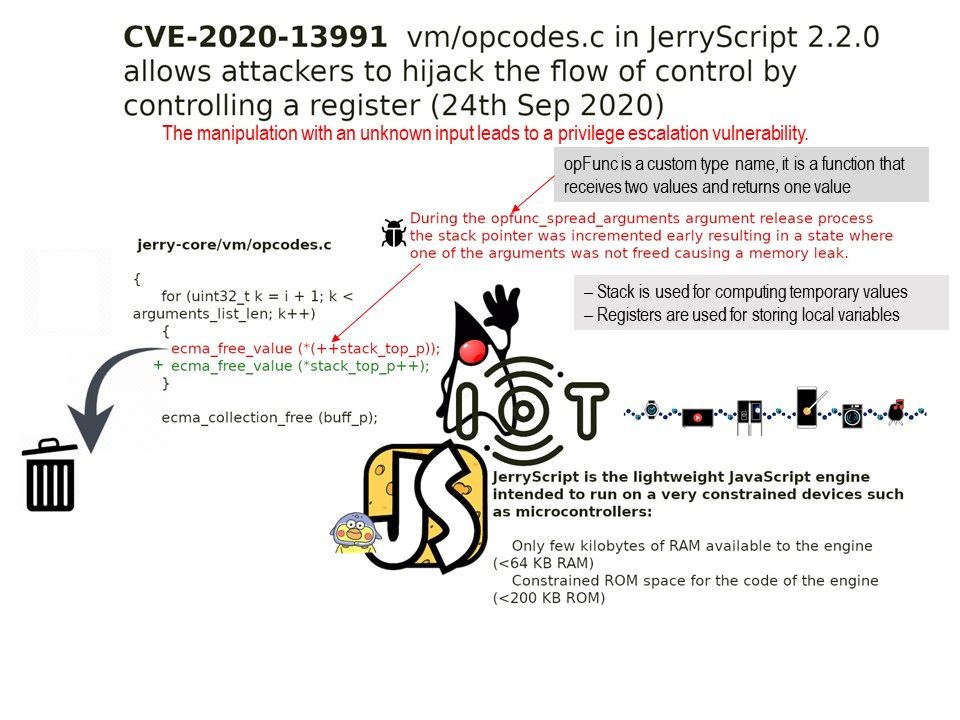
Preface: JerryScript is the lightweight JavaScript engine intended to run on a very constrained devices such as microcontrollers.
Background: In traditional programming environment.The source code is passed through a program called a compiler, which translates it into bytecode that the machine understands and can execute. Internet of Things devices have serious constraints on CPU performance and memory space. Therefore, Samsung designed the JerryScript engine, which can run on less than 64KB of memory, and all codes can be stored in less than 200KB of read-only memory (ROM).
JavaScript has no compilation step. Instead, an interpreter in the browser reads over the JavaScript code, interprets each line, and runs it.
Vulnerability: A vulnerability classified as critical has been found in JerryScript 2.2.0. This affects an unknown function of the file vm/opcodes.c. The manipulation with an unknown input leads to a privilege escalation vulnerability.
Remedy: On GitHub, Developer shown that it fixed. But there is no official announcement yet.