Preface: Why REST so popular? REST can be used over nearly any protocol, when used for web APIs it typically takes advantage of HTTP.
Canonical snapd technical features: Snap is a software deployment and package management system.It capable to deliver and update your app on any Linux distribution for desktop, cloud, and Internet of Things.
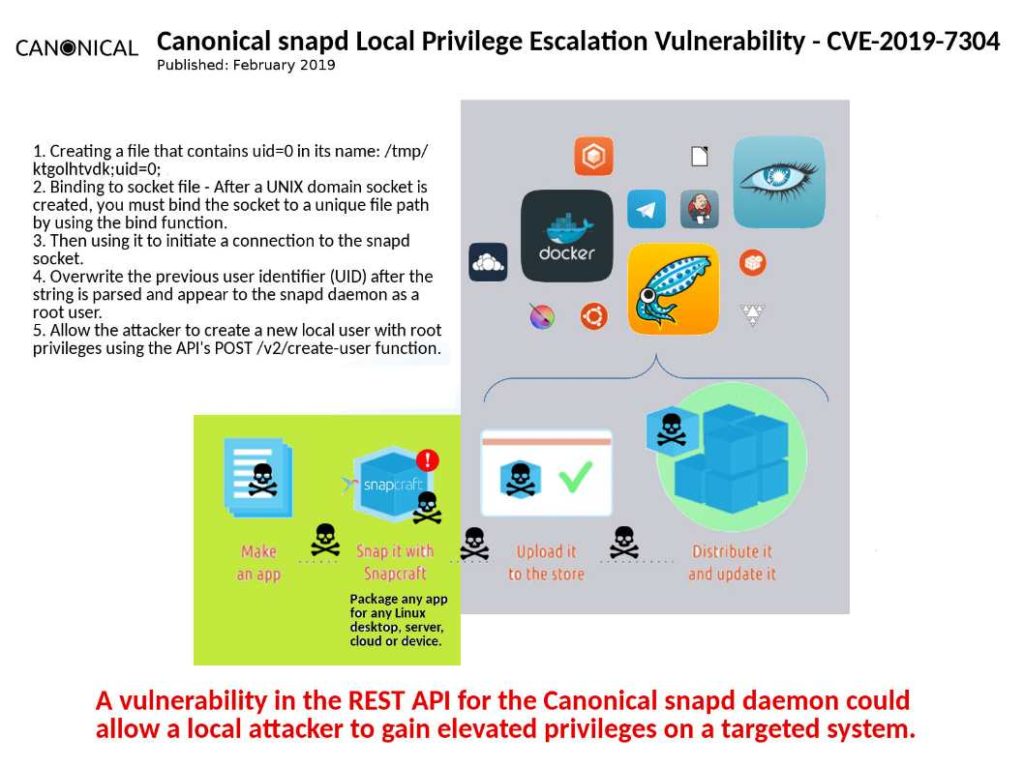
Vulnerability occurred:
- Creating a file that contains uid=0 in its name: /tmp/ktgolhtvdk;uid=0;
- Binding to socket file – After a UNIX domain socket is created, you must bind the socket to a unique file path by using the bind function.
- Then using it to initiate a connection to the snapd socket.
- Overwrite the previous user identifier (UID) after the string is parsed and appear to the snapd daemon as a root user.
- Allow the attacker to create a new local user with root privileges using the API’s POST /v2/create-user function.
Vendor Announcements: Canonical has released software updates at the following link.