Preface: Need to know what processes are running on a given machine? A servers current CPU temperature? Verify a hard drive is encrypted? OSQUERY can do, even though security monitoring.
Technical background: osquery is a tool that exposes an operating system as a high-performance relational database.The design founded by Facebook. It enables developers to write SQL-based queries that explore operating system data includes the following:
- Running processes
- Loaded kernel modules
- Open network connections
- Browser plugins
- Hardware events
- File hashes
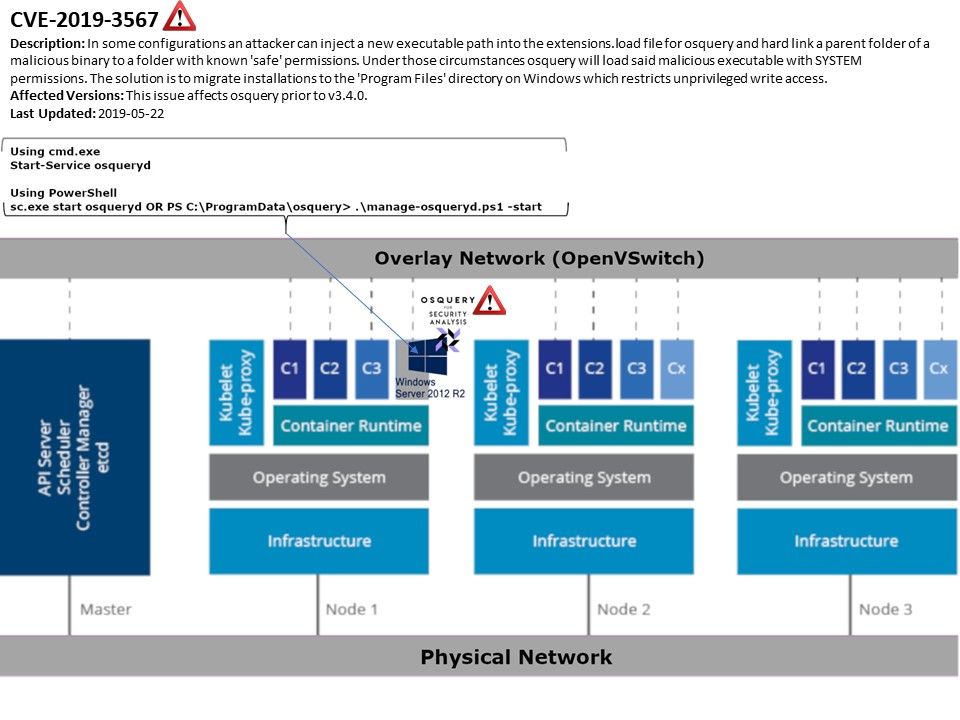
Vulnerability detail: Osquery running on windows or Linux system requires the daemon configured to be a system service. Meanwhile, this operation will make service daemon receive the system privileges. The design feature of osquery unintended let attacker has a way pass the file to a hard link parent folder. So it is similar to create a hidden area for malware. Under such circumstances the malware payload can be operate under SYSTEM permissions. The official announcement is as follows: https://www.facebook.com/security/advisories/cve-2019-3567