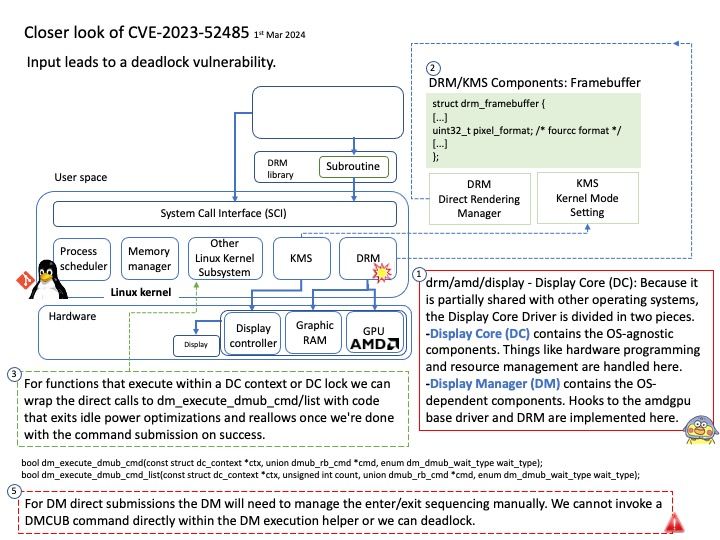
Preface: DRM and KMS
DRM stands for Direct Rendering Manager and was introduced to deal with graphic cards embedding GPUs
KMS stands for Kernel Mode Setting and is a sub-part of the DRM API
Background: The AMDgpu display manager, amdgpu_dm (or even simpler, dm) sits between DRM and DC. It acts as a liaison, converting DRM requests into DC requests, and DC responses into DRM responses.
Drm[/]amd[/]display – Display Core (DC): Because it is partially shared with other operating systems, the Display Core Driver is divided in two pieces.
-Display Core (DC) contains the OS-agnostic components. Things like hardware programming and resource management are handled here.
-Display Manager (DM) contains the OS-dependent components. Hooks to the amdgpu base driver and DRM are implemented here.
Vulnerability details: In the Linux kernel, the following vulnerability has been resolved: drm[/]amd[/]display: Wake DMCUB before sending a command
[Why] We can hang in place trying to send commands when the DMCUB isn’t powered on.
[How] For functions that execute within a DC context or DC lock we can wrap the direct calls to dm_execute_dmub_cmd[/]list with code that exits idle power optimizations and reallows once we’re done with the command submission on success. For DM direct submissions the DM will need to manage the enter[/]exit sequencing manually. We cannot invoke a DMCUB command directly within the DM execution helper or we can deadlock.
Official announcement: Please refer to the official announcement for details – https://nvd.nist.gov/vuln/detail/CVE-2023-52485