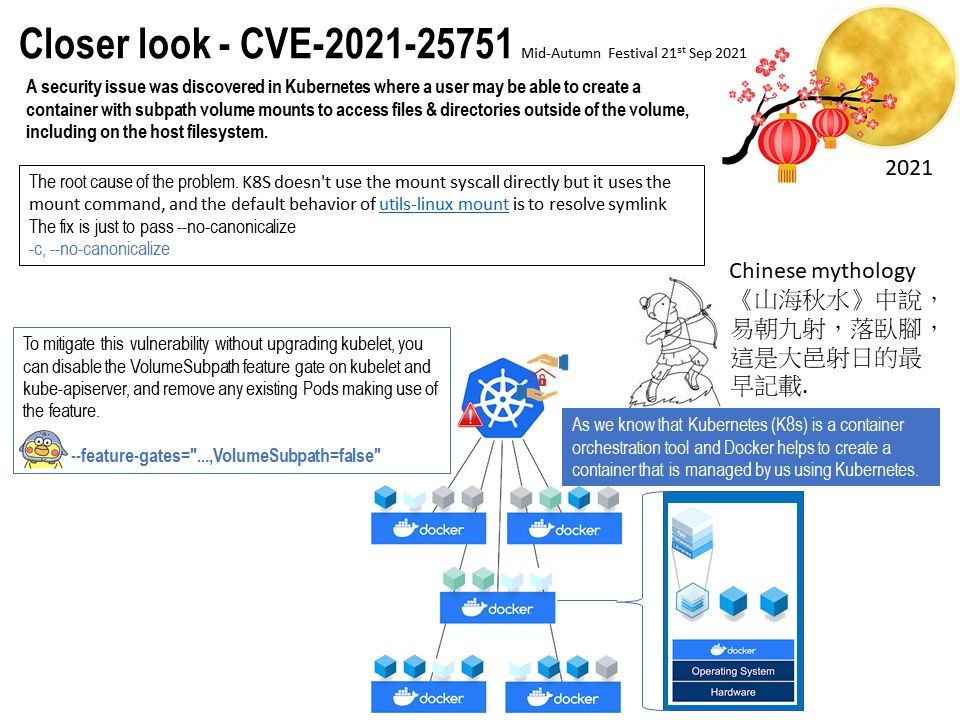
Preface: As we know that Kubernetes (K8s) is a container orchestration tool and Docker helps to create a container that is managed by us using Kubernetes.
Background: What is subPath in volume mount?
Subpath references files or directories that are controlled by the user, not the system. Volumes can be shared by containers that are brought up at different times in the Pod lifecycle, including by different Pods.
Kubernetes passes host paths to the container runtime to bind mount into the container.
Vulnerability details: A security issue was discovered in Kubernetes where a user may be able to create a container with subpath volume mounts to access files & directories outside of the volume, including on the host filesystem.
The root cause of the problem: K8S doesn’t use the mount syscall directly but it uses the mount command, and the default behavior of utils-linux mount is to resolve symlink.
Highlight: Don’t canonicalize paths. The mount command canonicalizes all paths (from command line or fstab) by default.
Remediation: To mitigate this vulnerability without upgrading kubelet, you can disable the VolumeSubpath feature gate on kubelet and kube-apiserver, and remove any existing Pods making use of the feature. Please refer to the attached picture for details.
Reference: Feature gates are a set of key=value pairs that describe Kubernetes features. You can turn these features on or off using the –feature-gates command line flag on each Kubernetes component.