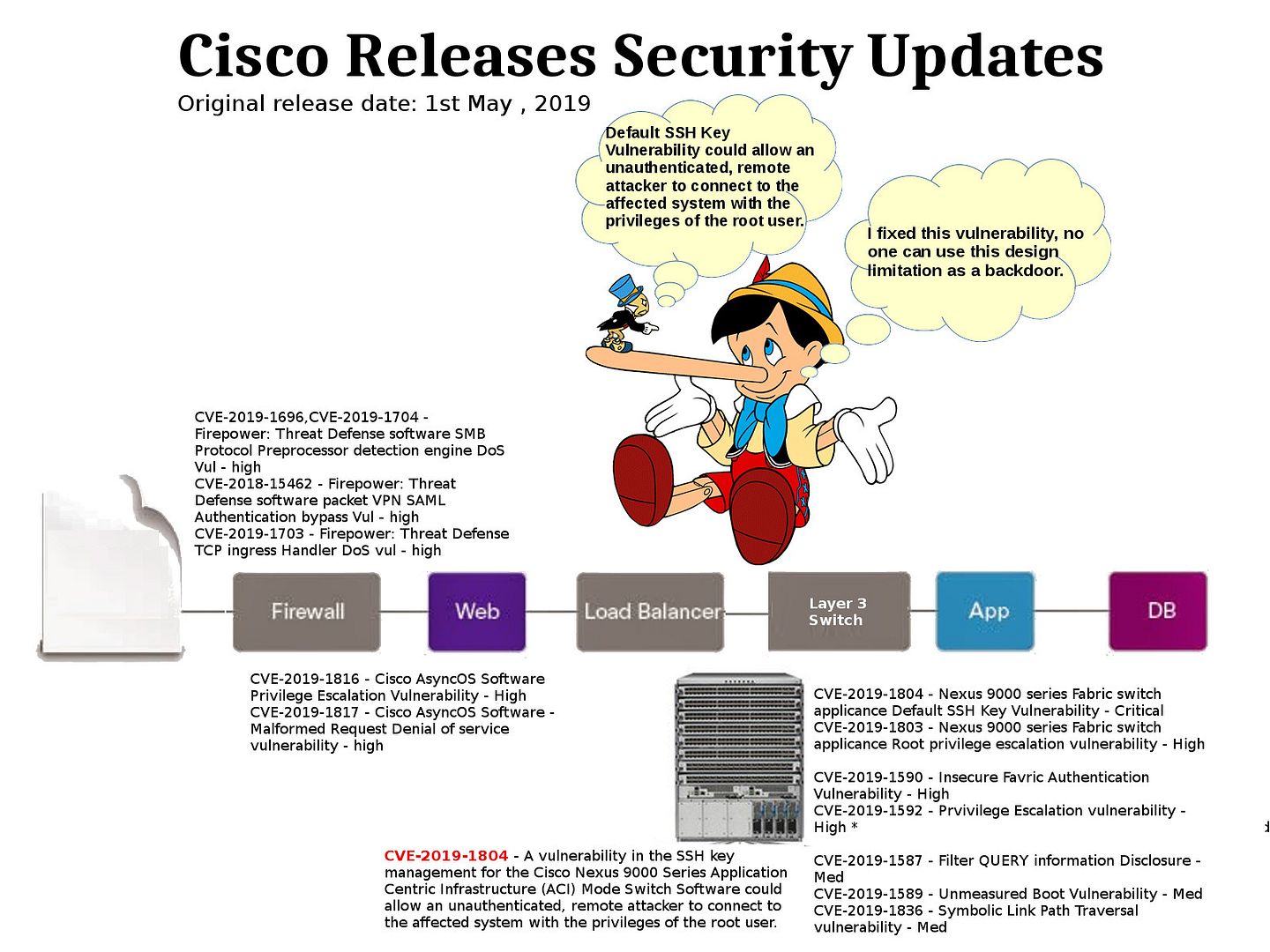
Preface: People judge an issue depends on your point of view. A design flaw or limitation of product in normal view point will make people dissatisfy. It is annoying and blame the designer what he is doing, does he dreaming?
From hacker point of view, the flaw can become a backdoor.
Highlight: CVE-2019-1804 – Cisco Nexus 9000 Series Fabric Switches Application Centric Infrastructure Mode Default SSH Key Vulnerability
Vulnerability details: The vulnerability occurs because default SSH key pair that is present in all devices. By default, most SSH implementations (e.g., OpenSSH) allow users to configure their own authorized key files (placing a public key in an account so they can access it using a private key). If organizations don’t keep an up to date inventory of authorized keys and regularly review it, users or even attackers may place authorized keys in unexpected places for future access.
Attention: For user who purchase directly from Cisco but do not hold a Cisco service contract. Do not worry, you should provides the product serial number and CVE reference number to Cisco as evidence of entitlement to a free upgrade. Besides, ther are many security update this week, please contact your cisco partner for update details.
Reference: Official announcement – https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20190501-nexus9k-sshkey