Preface: NVIDIA DGX-1 is an integrated deep learning workstation with a large computing capacity, which can be used to run demanding deep learning workloads. It provides GPU computing power of 1 PetaFLOPS (1 quadrillion floating-point operations per second).
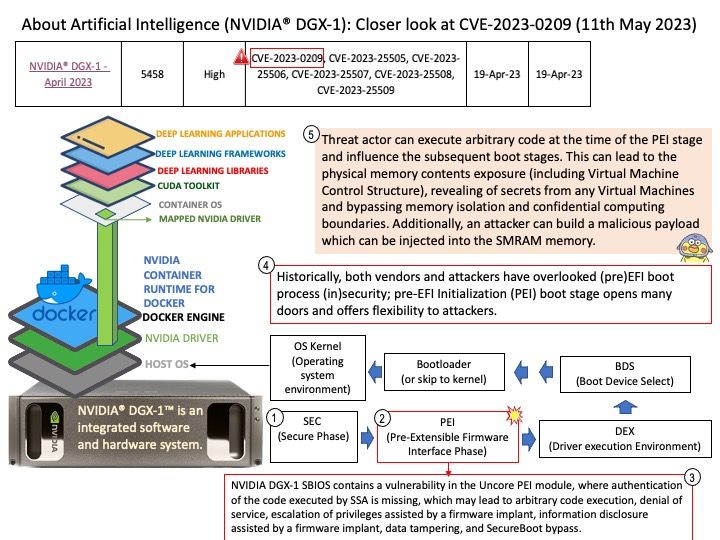
Background: Historically, both vendors and attackers have overlooked (pre)EFI boot process (in)security; pre-EFI Initialization (PEI) boot stage opens many doors and offers flexibility to attackers.
The Pre-EFI Initialization (PEI) phase provides a standardized method of loading and invoking specific initial configuration routines for the processor, chipset, and system board. The PEI phase occurs after the Security (SEC) phase. The primary purpose of code operating in this phase is to initialize enough of the system to allow instantiation of the Driver Execution Environment (DXE) phase.
The Driver Execution Environment (DXE) phase is where most of the system initialization is performed. Pre-EFI Initialization (PEI), the phase prior to DXE, is responsible for initializing permanent memory in the platform so that the DXE phase can be loaded and executed.
Note: Security (SEC) and Pre-EFI (PEI) phases – both are controlled by the firmware vendor.
SEC – Init CPU, clear caches, load BIOS ROM
PEI – Initialize chipset, RAM, devices, Secure Boot (Record Secure Boot in PCR 7)
Vulnerability details: NVIDIA DGX-1 SBIOS contains a vulnerability in the Uncore PEI module, where authentication of the code executed by SSA is missing, which may lead to arbitrary code execution, denial of service, escalation of privileges, information disclosure, data tampering, and SecureBoot bypass.
Official announcement: For details, please refer to the link – https://nvidia.custhelp.com/app/answers/detail/a_id/5458