Preface: ESXi is not built upon the Linux kernel, but uses an own VMware proprietary kernel (the VMkernel) and software, and it misses most of the applications and components that are commonly found in all Linux distributions.
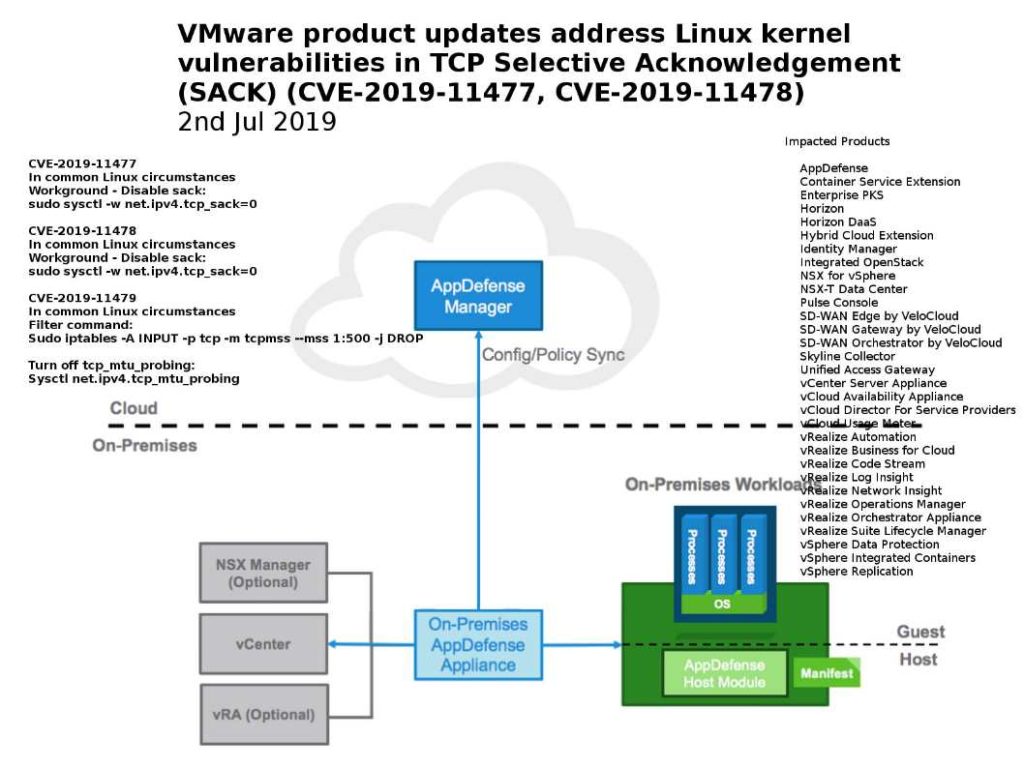
In common Linux circumstances to avoid SACK vulnerabilities. The workaround are:
CVE-2019-11477
Workground – Disable sack:
sudo sysctl -w net.ipv4.tcp_sack=0
CVE-2019-11478
Workground – Disable sack:
sudo sysctl -w net.ipv4.tcp_sack=0
CVE-2019-11479
Filter command:
Sudo iptables -A INPUT -p tcp -m tcpmss –mss 1:500 -j DROP
Turn off tcp_mtu_probing:
Sysctl net.ipv4.tcp_mtu_probing
Perhaps this is VMWARE. So you must follow below solution by vendor.
https://www.vmware.com/security/advisories/VMSA-2019-0010.html