Preface: Is io_uring secure? io_uring has produced many security problems. Google has found it necessary to either completely forego io_uring or severely limit its use to trusted code.
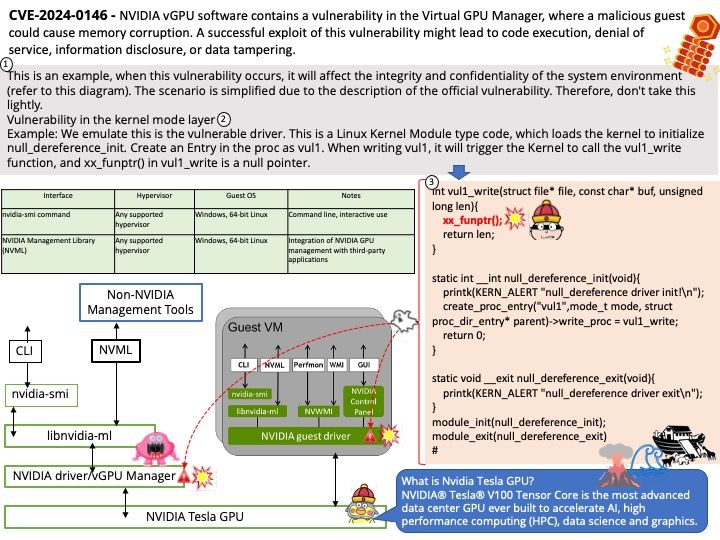
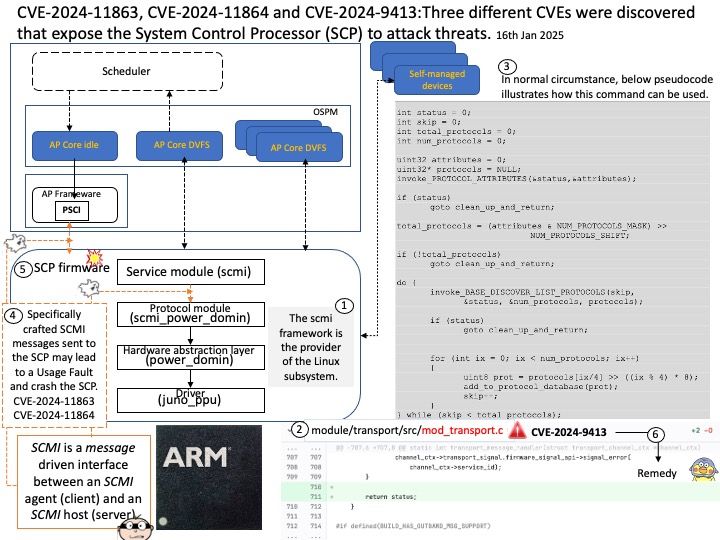
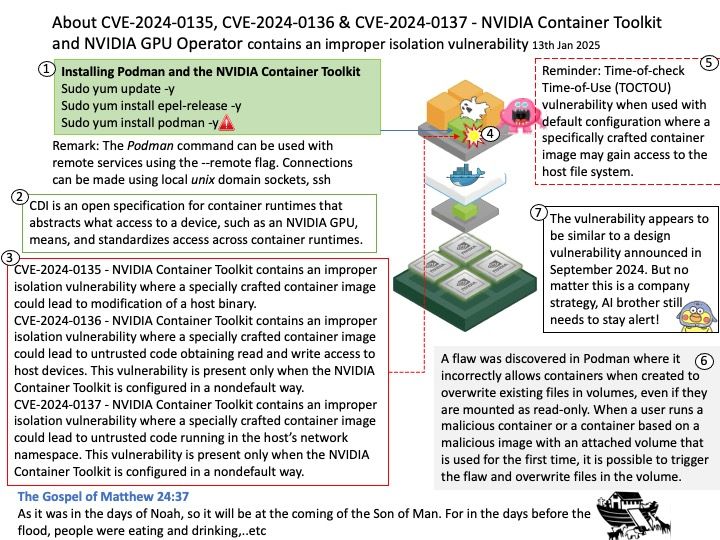
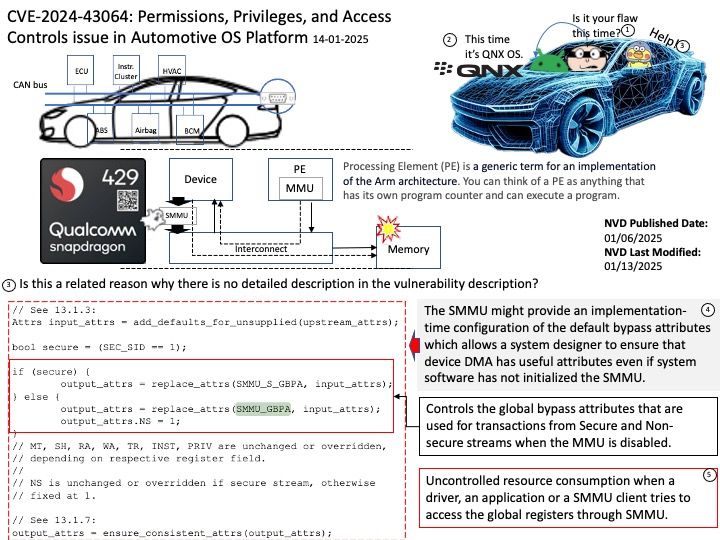
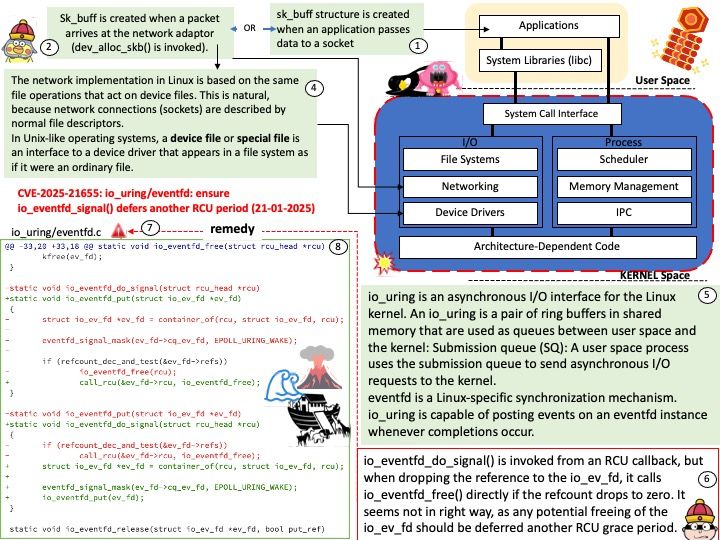
Background: io_uring is an asynchronous I/O interface for the Linux kernel. An io_uring is a pair of ring buffers in shared memory that are used as queues between user space and the kernel: Submission queue (SQ): A user space process uses the submission queue to send asynchronous I/O requests to the kernel.
eventfd(2) is a Linux-specific synchronization mechanism. io_uring is capable of posting events on an eventfd instance whenever completions occur.
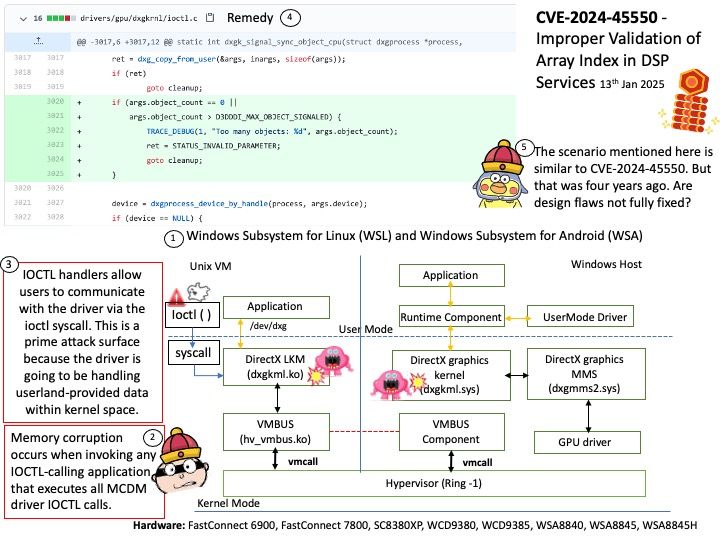
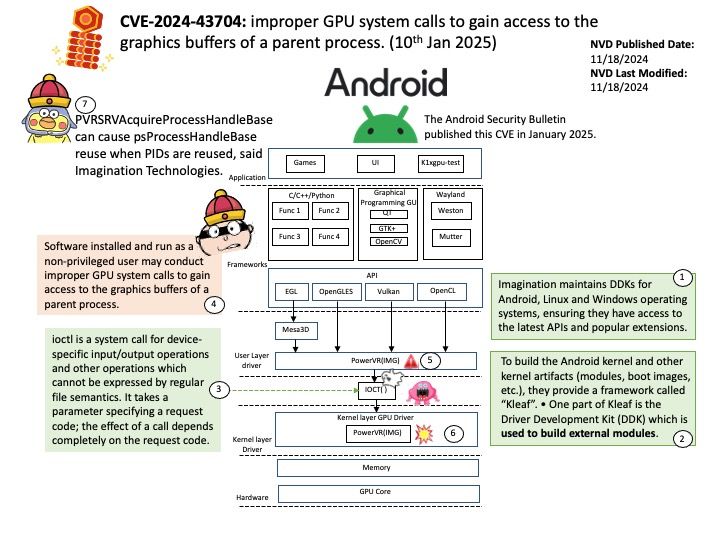
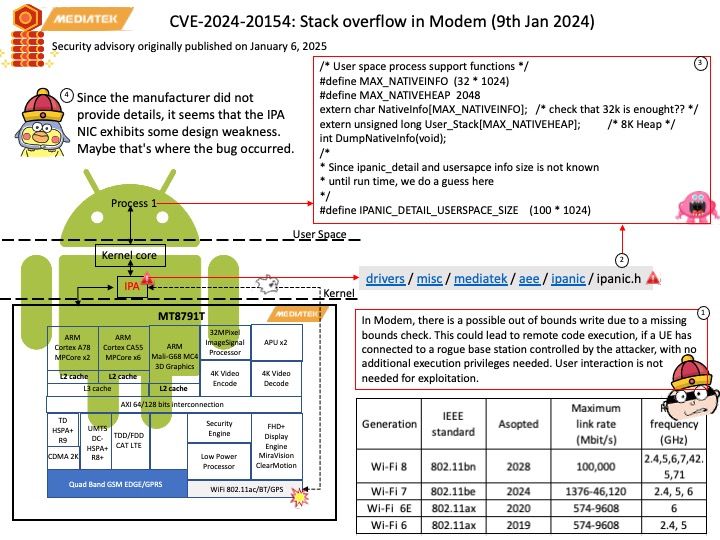
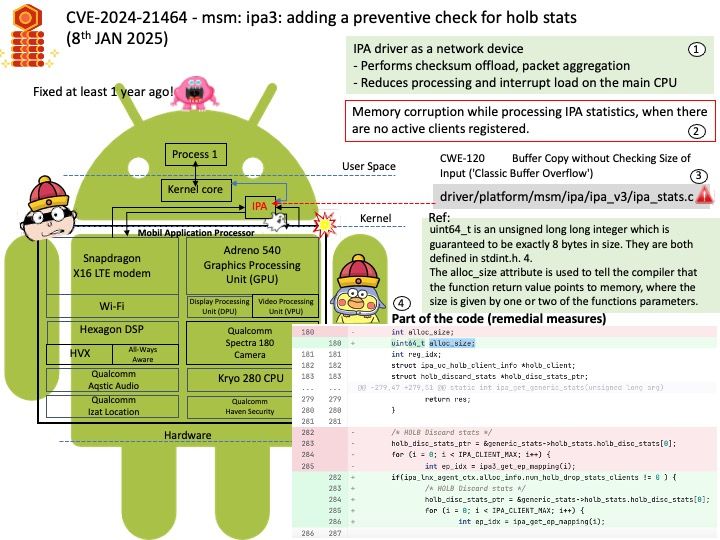
Vulnerability details: In the Linux kernel, the following vulnerability has been resolved: io_uring/eventfd: ensure io_eventfd_signal() defers another RCU period io_eventfd_do_signal() is invoked from an RCU callback, but when dropping the reference to the io_ev_fd, it calls io_eventfd_free() directly if the refcount drops to zero. This isn’t correct, as any potential freeing of the io_ev_fd should be deferred another RCU grace period. Just call io_eventfd_put() rather than open-code the dec-and-test and free, which will correctly defer it another RCU grace period.
Official announcement: Please refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2025-21655